Introduction
This chapter introduces the atomic purple teaming methodology. It explores the applications for the methodology, as well as inputs that may help you shape your exercises. The chapter considers what an exercise targeting enumeration of the Domain Admins Active Directory group might look like, and how you can evaluate your test suites to ensure they provide the breadth and depth required.
The chapter considers key metrics to capture when performing your atomic testing, and also highlights micro-emulation as a hybrid form of purple team testing that can help overcome some of the shortfalls of ‘pure’ atomic tests.
The complete test suite produced in this chapter can be found here:
Domain Admins enumeration techniques
| Test name | Command | Type |
|---|---|---|
A net command with a shortened domain flag |
net group "domain admins" /dom |
net |
A net command with a reordered flag |
net group /domain "domain admins" |
net |
An obfuscatednet command |
set GROUP="Domain Admins"n^e^t g^r^o^u^p %GROUP% /d^o |
net |
| An ADSI searcher script |
$Group = [ADSI]"LDAP://CN=Domain Admins, CN=Users, DC=Contoso,DC=com"$Group.member | ForEach-Object {$Searcher = [adsisearcher]"(distinguishedname=$_)"$Searcher.FindOne().Properties.cn} |
PowerShell |
| An RSAT Active Directory cmdlet | Get-ADGroupMember -Identity "Domain Admins" |
PowerShell |
| A PowerView command | Get-DomainGroupMember "Domain Admins" |
PowerShell |
| An AdFind command |
AdFind.exe -b "CN=Domain Admins, CN=Users, DC=Contoso, DC=com" member
|
AdFind |
| The use of StandIn |
execute-assembly /tools/StandIn.exe --group "Domain Admins"
|
In-memory .NET execution |
| The use of Ldapsearch | ldapsearch "CN=Domain Admins" member |
BOF |
| The use of Recon-AD | Recon-AD-Groups Domain Admins |
Reflective DLL |
| The use of SOCKS with Impacket net.py |
socks 8080 (on Cobalt Strike beacon)proxychains python net.py user:pass@dc group -name “Domain Admins” (on attacker host command line)
|
SOCKS and Impacket |
Chapter Content
This section provides reproductions of the key figures and code snippets seen in this chapter.
Scoping and Dechaining
Generating Test Cases
net.exe
The complete Sigma rule for detecting reconnaissance performed with the net.exe and net1.exe binaries.
| Sourced from: https://github.com/SigmaHQ/sigma/blob/fad4742996c55d8d4663e611f84877a2b741dc46/rules/windows/process_creation/proc_creation_win_net_groups_and_accounts_recon.yml |
title: Suspicious Group And Account Reconnaissance Activity Using Net.EXE
id: d95de845-b83c-4a9a-8a6a-4fc802ebf6c0
status: test
description: |
Detects suspicious reconnaissance command line activity on Windows systems using Net.EXE
Check if the user that executed the commands is suspicious (e.g. service accounts, LOCAL_SYSTEM)
references:
- https://redcanary.com/blog/how-one-hospital-thwarted-a-ryuk-ransomware-outbreak/
- https://thedfirreport.com/2020/10/18/ryuk-in-5-hours/
- https://research.nccgroup.com/2022/08/19/back-in-black-unlocking-a-lockbit-3-0-ransomware-attack/
author: Florian Roth (Nextron Systems), omkar72, @svch0st, Nasreddine Bencherchali (Nextron Systems)
date: 2019-01-16
modified: 2023-03-02
tags:
- attack.discovery
- attack.t1087.001
- attack.t1087.002
logsource:
category: process_creation
product: windows
detection:
selection_img:
- Image|endswith:
- '\net.exe'
- '\net1.exe'
- OriginalFileName:
- 'net.exe'
- 'net1.exe'
# Covers group and localgroup flags
selection_group_root:
CommandLine|contains:
- ' group '
- ' localgroup '
selection_group_flags:
CommandLine|contains:
# Add more groups for other languages
- 'domain admins'
- ' administrator' # Typo without an 'S' so we catch both
- ' administrateur' # Typo without an 'S' so we catch both
- 'enterprise admins'
- 'Exchange Trusted Subsystem'
- 'Remote Desktop Users'
- 'Utilisateurs du Bureau à distance' # French for "Remote Desktop Users"
- 'Usuarios de escritorio remoto' # Spanish for "Remote Desktop Users"
- ' /do' # short for domain
filter_group_add:
# This filter is added to avoid the potential case where the point is not recon but addition
CommandLine|contains: ' /add'
# Covers 'accounts' flag
selection_accounts_root:
CommandLine|contains: ' accounts '
selection_accounts_flags:
CommandLine|contains: ' /do' # short for domain
condition: selection_img and ((all of selection_group_* and not filter_group_add) or all of selection_accounts_*)
falsepositives:
- Inventory tool runs
- Administrative activity
level: medium
PowerShell
A code snippet to enumerate Domain Admin members with PowerShell:
$Group = [ADSI]"LDAP://CN=Domain Admins,CN=Users,DC=Contoso,DC=com"
$Group.member | ForEach-Object {
$Searcher = [adsisearcher]"(distinguishedname=$_)"
$Searcher.FindOne().Properties.cn
}
Domain enumeration via the Active Directory PowerShell module:
Get-ADGroupMember -Identity "Domain Admins"
Use of PowerSploit to enumerate Domain Admins:
Get-DomainGroupMember "Domain Admins"
Evaluating Test Suites
Attack Sophistication
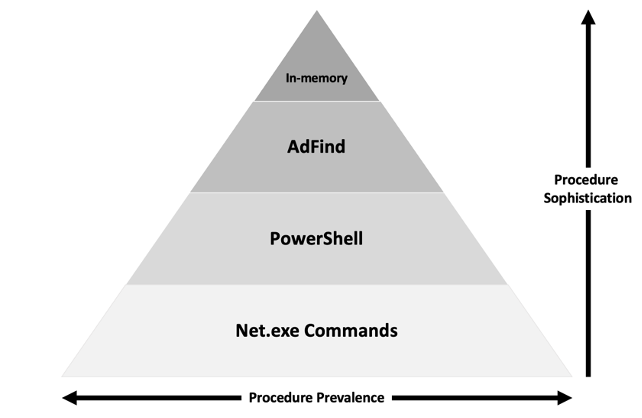
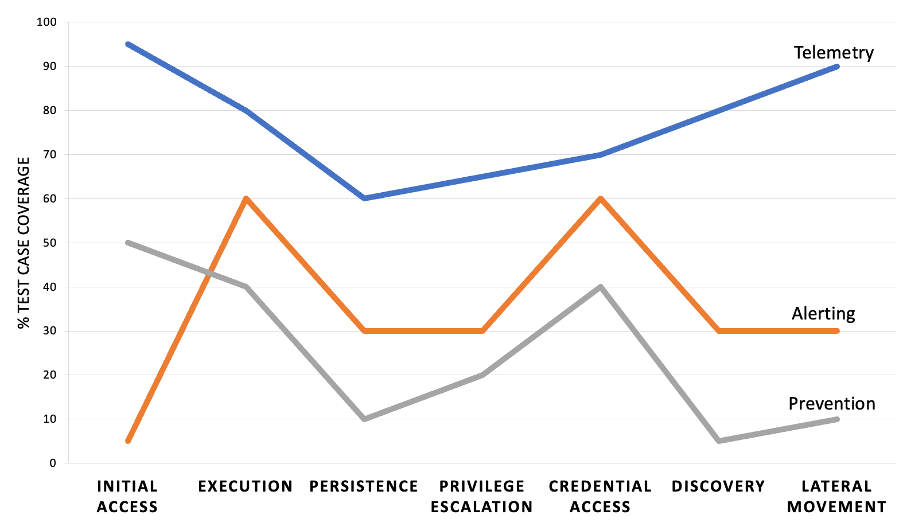
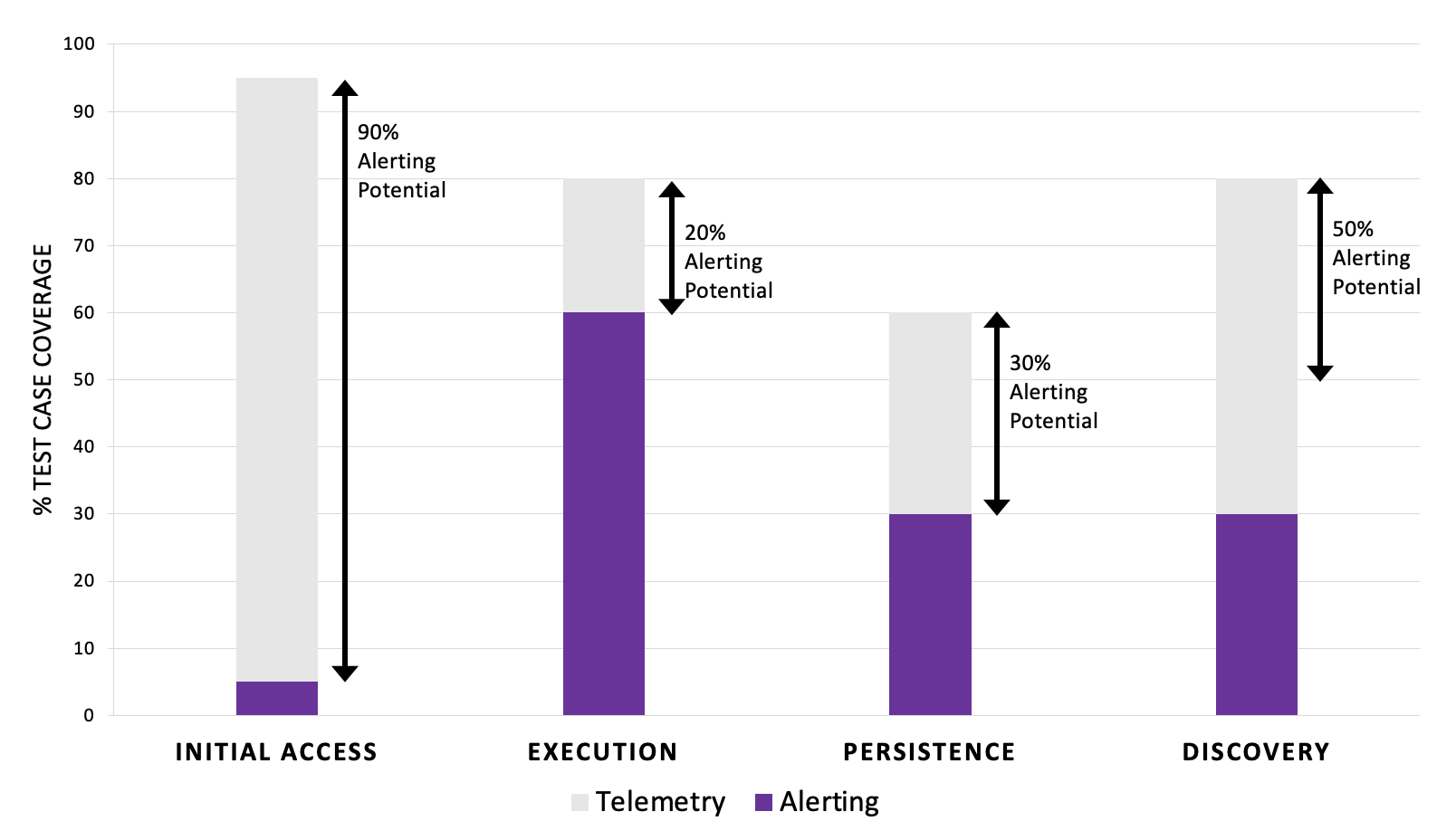
Plotting Results
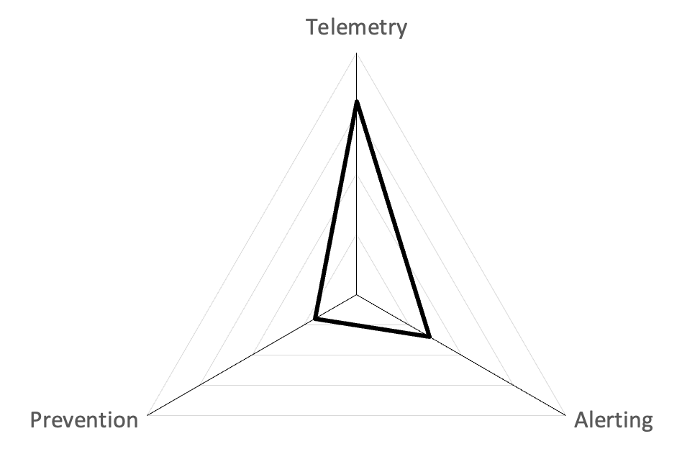
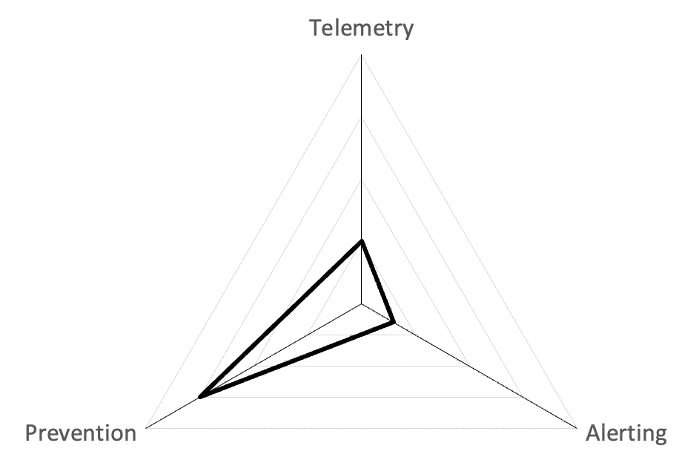
Resources
The following resources expand on topics covered in this chapter.
Applications of Atomic Purple Teaming
Techniques for breaking out of Citrix environments
Michael Yardley, "Breaking Out of Citrix and other Restricted Desktop Environments," Pen Test Partners, June 6, 2014
Read MoreScoping and Dechaining
Examples of the many techniques for performing HTML smuggling
Alfie Champion, "HTML Smuggling: Recent observations of threat actor techniques," delivr.to, January 6, 2023
Read MoreOperational considerations and technical implementation details of environmental keying and execution guardrails
Brandon McGrath, "Execution Guardrails: No One Likes Unintentional Exposure," TrustedSec, August 6, 2024
Read MoreInputs
A whitepaper covering the extensive abuse potential of misconfigured Active Directory Certificate Services (ADCS)
Will Schroeder, Lee Chagolla-Christensen, "Certified Pre-Owned," SpecterOps, June 22, 2022
Read MoreA collection of post-exploitation techniques targeting components of the identify provider, Okta
Adam Chester, "Okta for Red Teamers," TrustedSec, September 18, 2023
Read MoreGenerating Test Cases
Examples of command line obfuscation techniques
Daniel Bohannon, "DOSfuscation: Exploring the Depths of Cmd.exe Obfuscation and Detection Techniques," Mandiant, 2019
Read MoreA Sigma rule to detect the enumeration of high value groups like enterprise and domain administrators via the built-in net.exe executable
Florian Roth, omkar72, @svch0st, Nasreddine Bencherchali, "proc_creation_win_net_groups_and_accounts_recon.yml", GitHub, accessed January 12, 2025
Read MoreAn overview of detection and prevention mechanisms introduced by Microsoft in Windows PowerShell version 5 and onwards
"PowerShell loves the Blue Team," Microsoft, June 9, 2015
Read MoreAn overview of the architecture and impact of the Antimalware Scan Interface
"How the Antimalware Scan Interface (AMSI) helps you defend against malware," Microsoft, August 23, 2019
Read MoreIntroducing execute-assembly to Cobalt Strike
Raphael Mudge, "Cobalt Strike 3.11 – The snake that eats its tail," Cobalt Strike, April 9, 2018
Read MoreIntroducing Beacon Object Files to Cobalt Strike v4.1
Raphael Mudge, "Cobalt Strike 4.1 – The Mark of Injection," Cobalt Strike, June 25, 2020
Read MoreEvaluating Test Suites
Introducing the concept of capability abstraction
Jared Atkinson, "Capability Abstraction," SpecterOps, Feb 6, 2020
Read MorePlotting Results
Guidance on the detection and prevention of web shell malware
Australian Signals Directorate, "Detect and Prevent Web Shell Malware," Australian Signals Directorate, June 9, 2020
Read MoreMicro-Emulation
Release of the micro-emulation framework from the Center for Threat-informed Defense
Mike Cunningham and Jamie Williams, "Ahhh, This Emulation is Just Right: Introducing Micro Emulation Plans," September 15, 2022
Read MoreA micro-emulation plan replicating web shell activity
"Micro Emulation Plan: Web Shells", GitHub, accessed January 12, 2025
Read MoreA micro-emulation plan replicating the popular C2 framework technique Fork-n-Run
"Micro Emulation Plan: Named Pipes", GitHub, accessed January 12, 2025
Read MoreA micro-emulation plan replicating Active Directory enumeration through LDAP queries, Windows APIs and built-in executables
"Micro Emulation Plan: Active Directory Enumeration", GitHub, accessed January 12, 2025
Read MoreA micro-emulation plan replicating user-driven execution of an initial access payload that could be delivered via phishing
"Micro Emulation Plan: User Execution", GitHub, accessed January 12, 2025
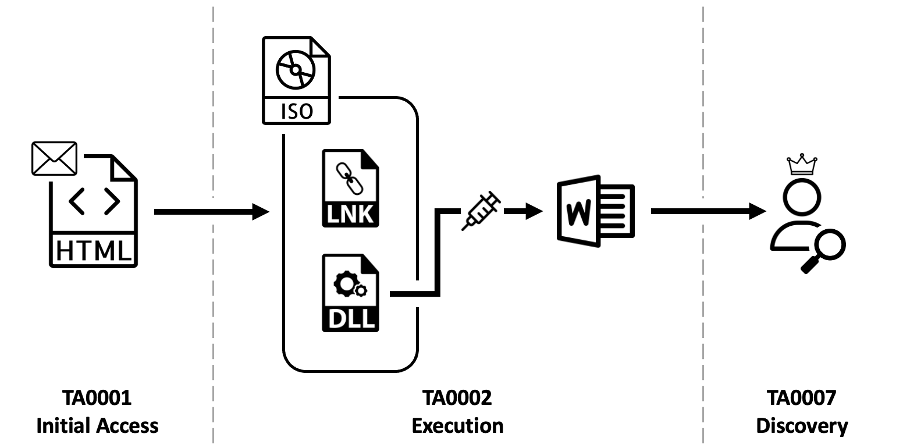
Read MoreDemonstration of IcedID malware delivery via an ISO disk image file, designed to bypass Mark of the Web
"Malicious ISO File Leads to Domain Wide Ransomware", The DFIR Report, April 3, 2023
Read MoreAnother example of disk image based initial compromise to delivery QakBot malware
"Surge of QakBot Activity Using Malspam, Malicious XLSB Files", Center for Internet Security, accessed January 12, 2025
Read MoreBumblebee malware infection achieved via an LNK and DLL file contained in an ISO disk image
"Malicious ISO File Leads to Domain Wide Ransomware", The DFIR Report, September 26, 2022
Read MoreAn article covering a Microsoft 'Patch Tuesday' in which the Mark of the Web bypass for ISO disk images was patched
"Microsoft fixes Windows zero-day bug exploited to push malware", BleepingComputer, November 22, 2022
Read More