Introduction
This chapter provides an overview of key frameworks that enable the community to analyze, track and better articulate adversary activity. Frameworks like David J Bianco’s Pyramid of Pain also allow you to better evaluate the scope of your detections. All of this plays a key role in how threat intelligence, detection engineering and adversary emulation teams work together.
Chapter Content
This section provides reproductions of the key figures and code snippets seen in this chapter.
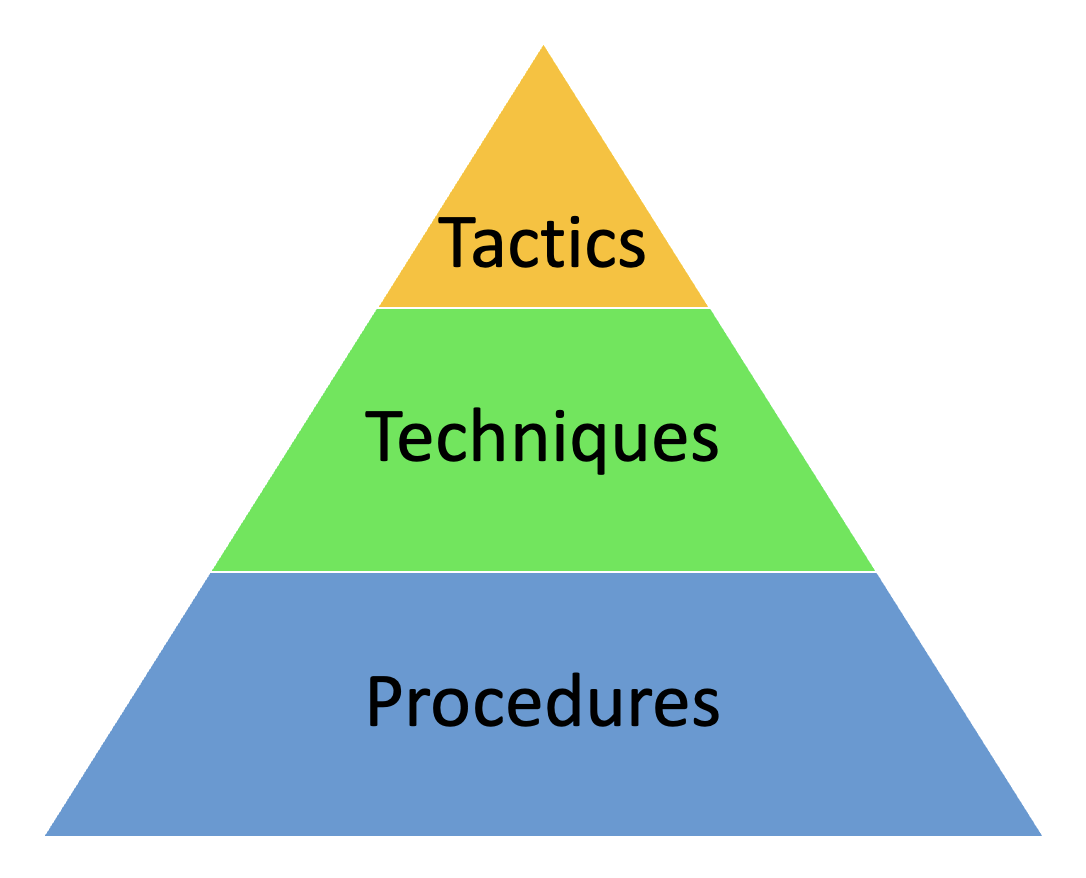
Tactics Techniques, and Procedures
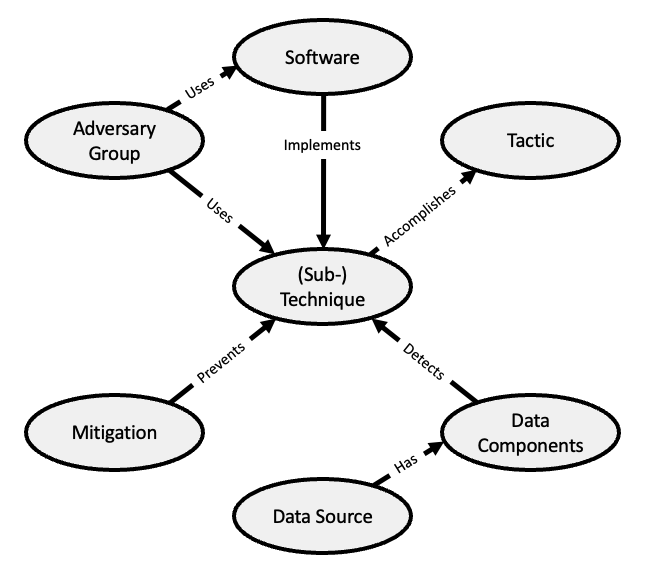
MITRE ATT&CK
Object Relationships
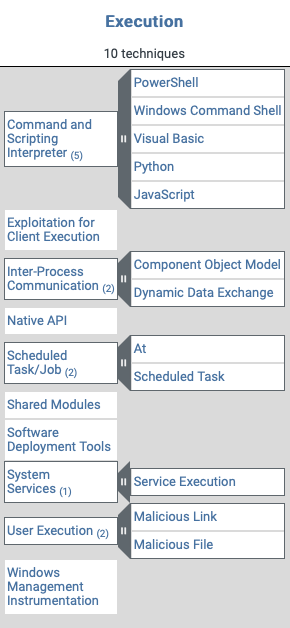
Techniques and Sub-techniques
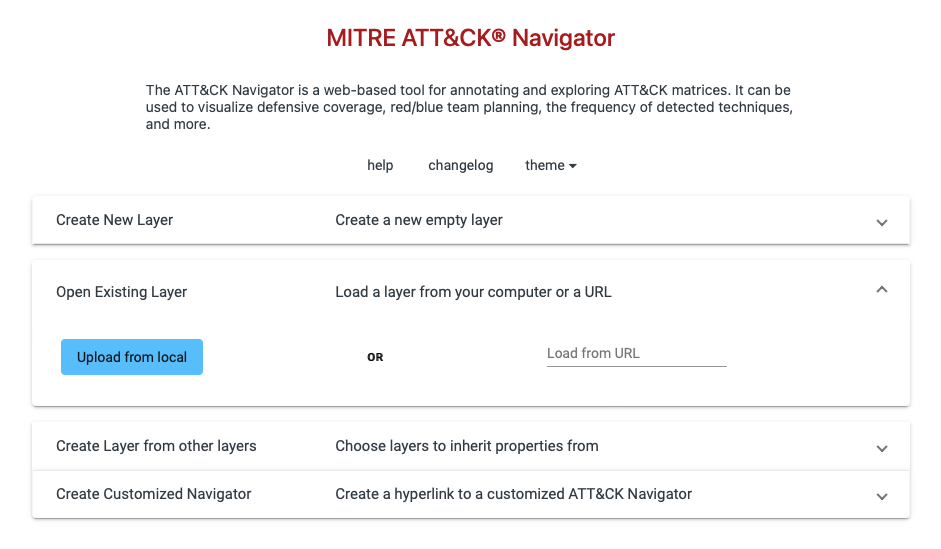
Navigator
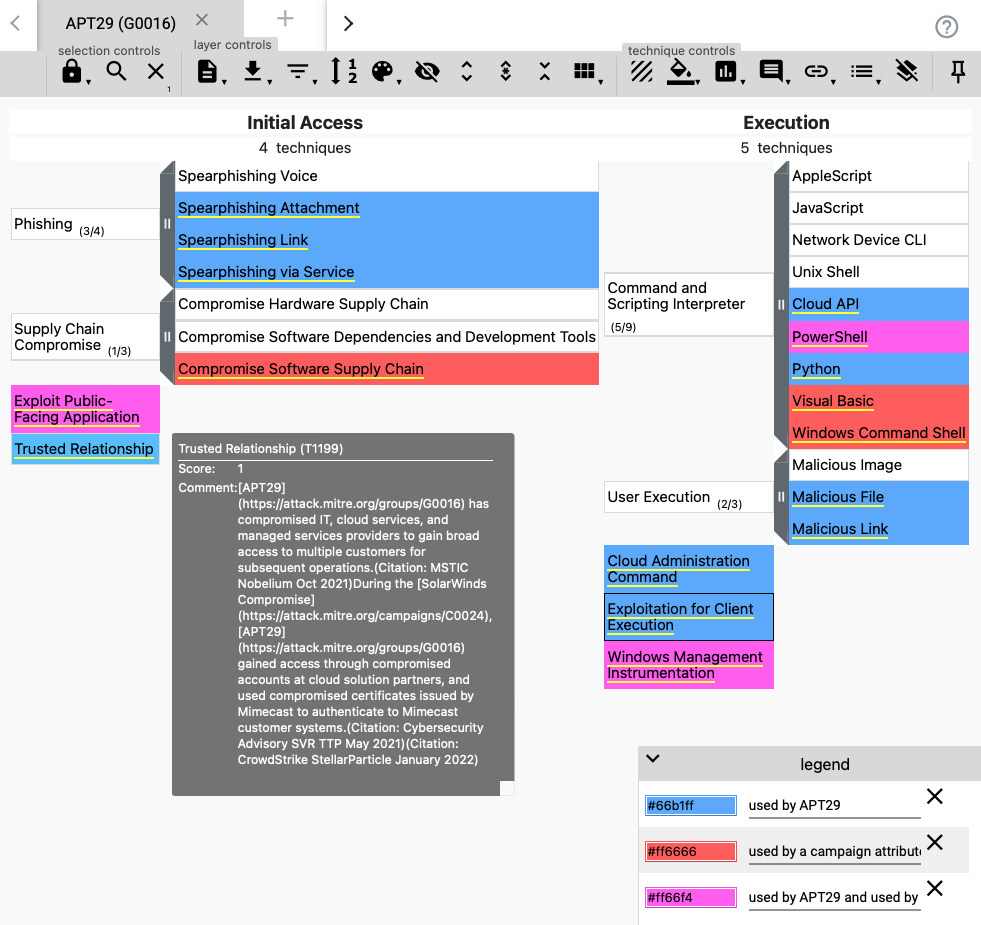
ATT&CK Tools
D3FEND
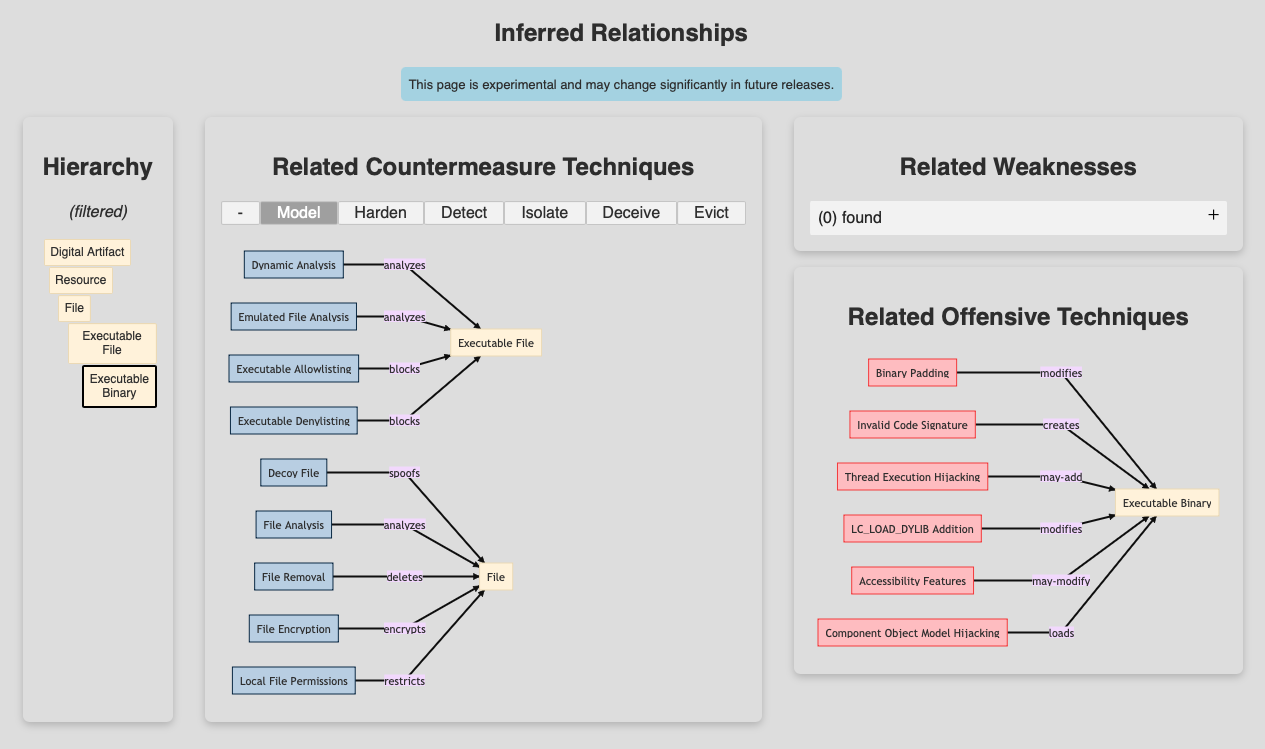
Cyber Analytics Repository
A pseudocode implementation of an analytic used to detect the dumping of the LSASS process with a utility called ProcDump:
processes = search Process:Create
procdump_lsass = filter processes where (
exe = "procdump*.exe" and
command_line = "*lsass*")
output procdump_lsass
The Diamond Model of Intrusion Analysis
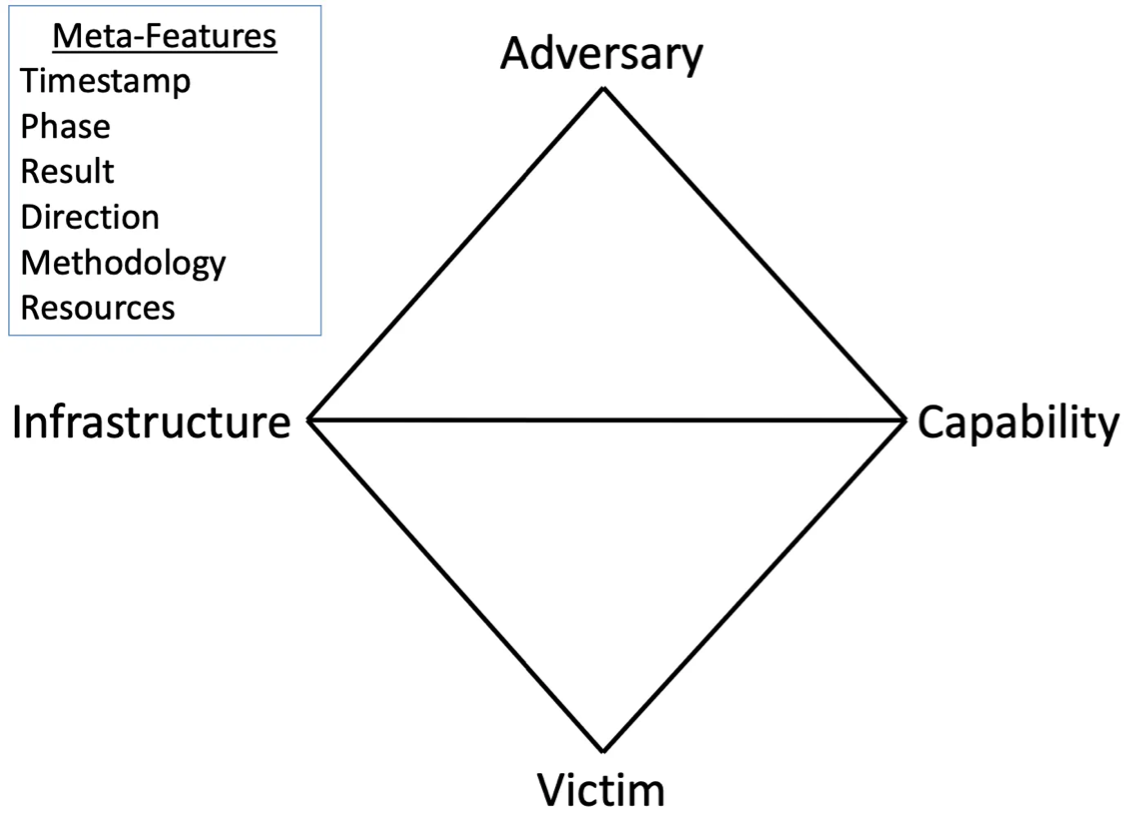
Extended Model
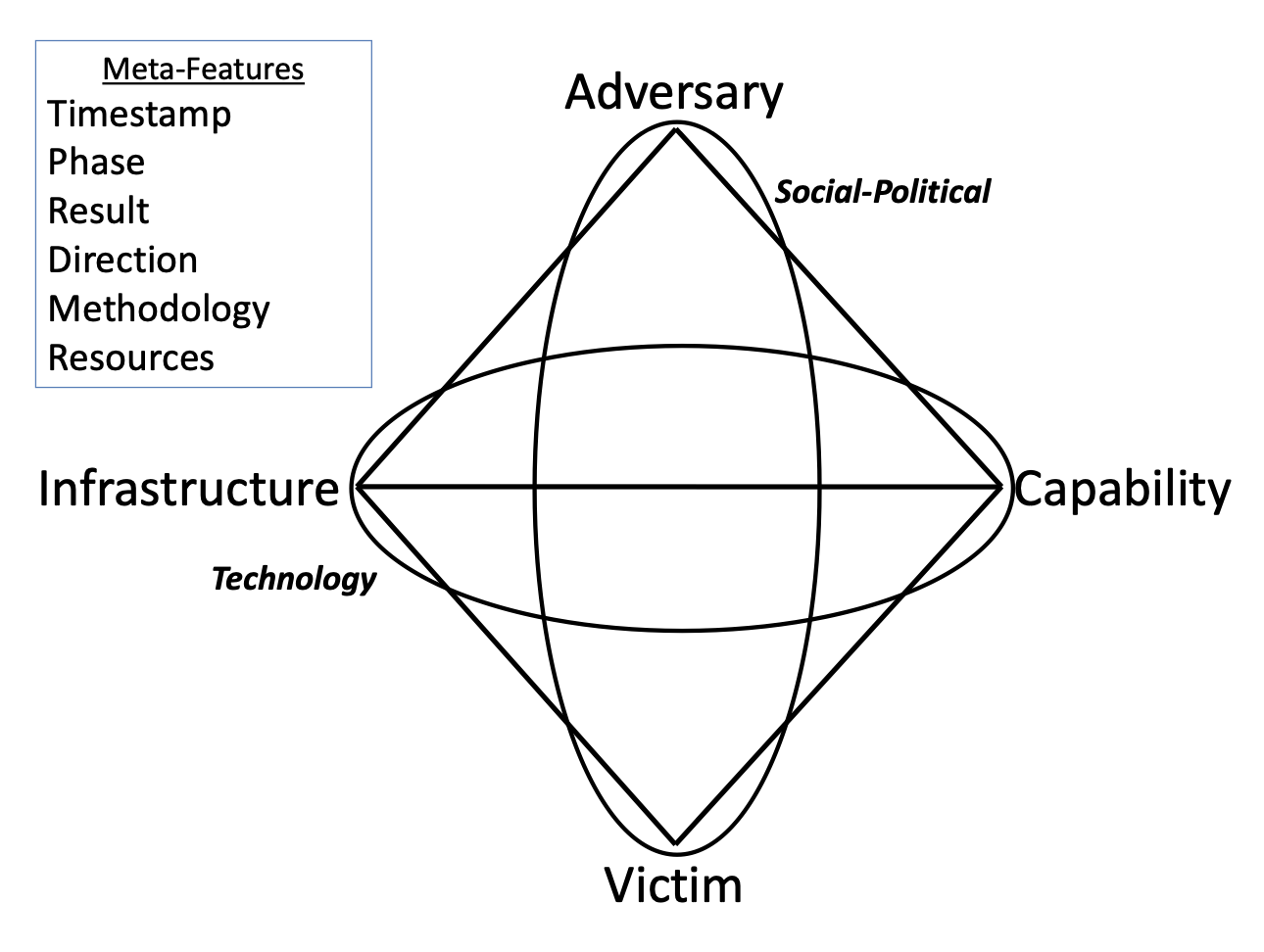
Activity Threads
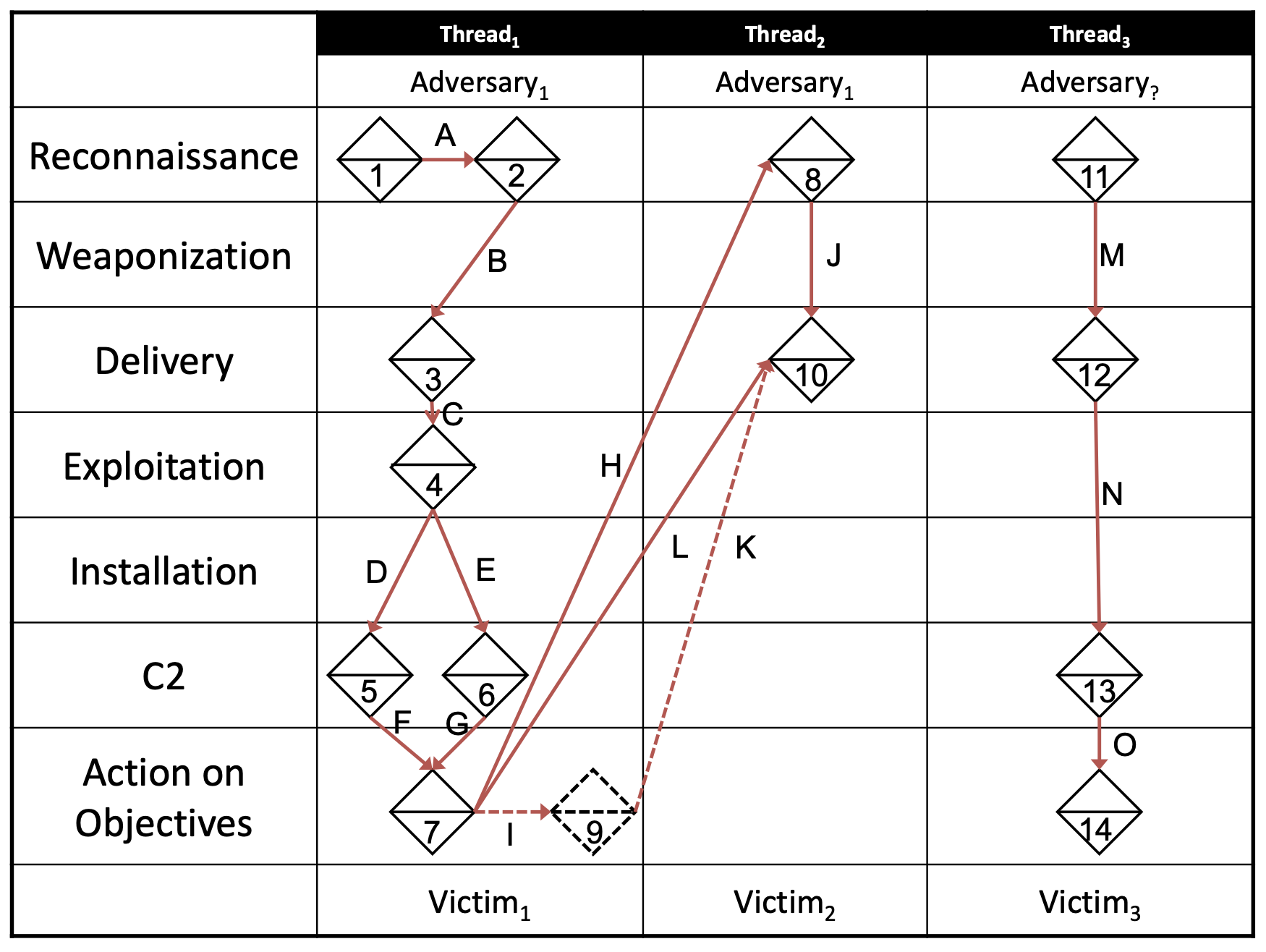
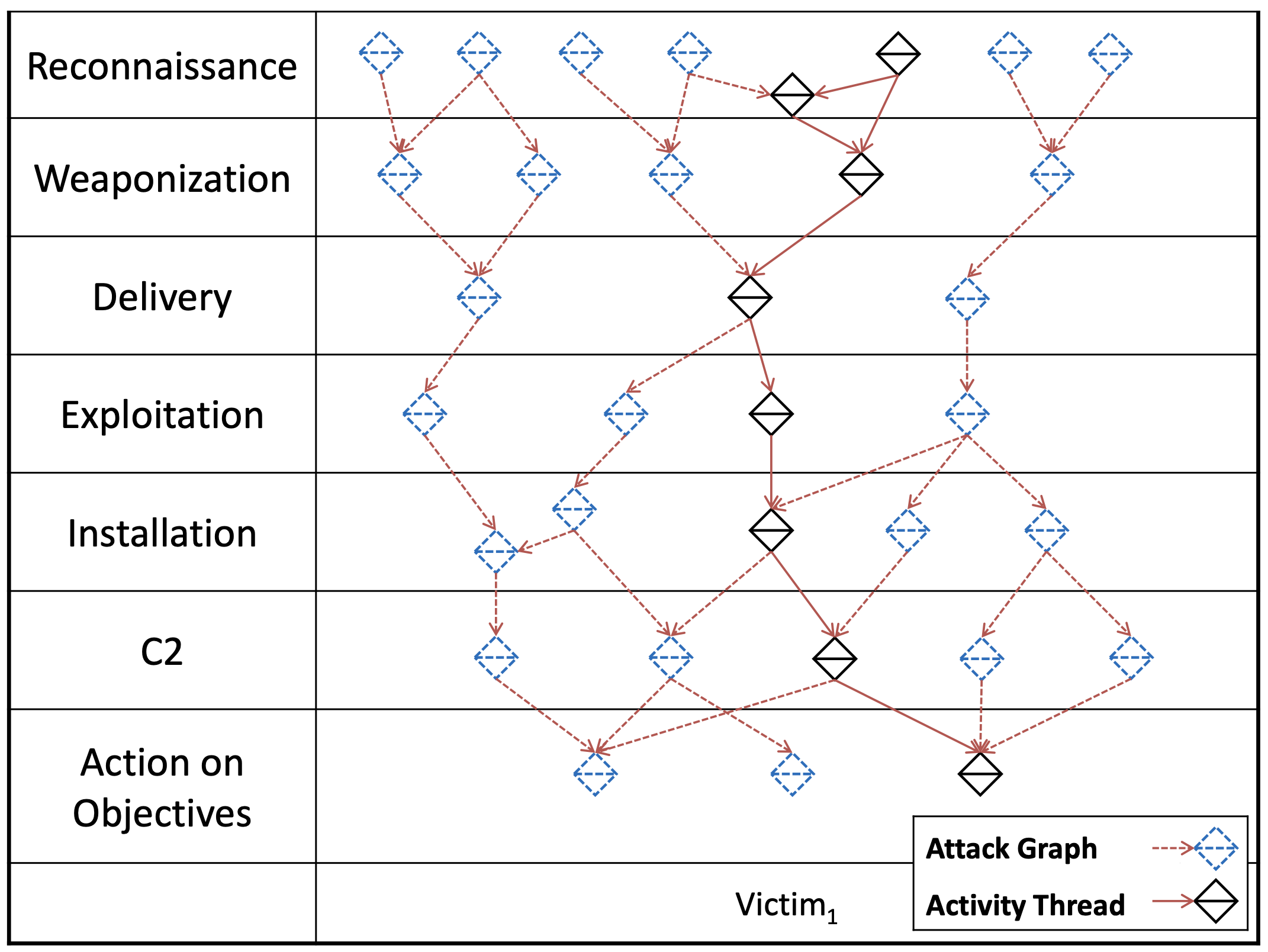
Activity-Attack Graphs
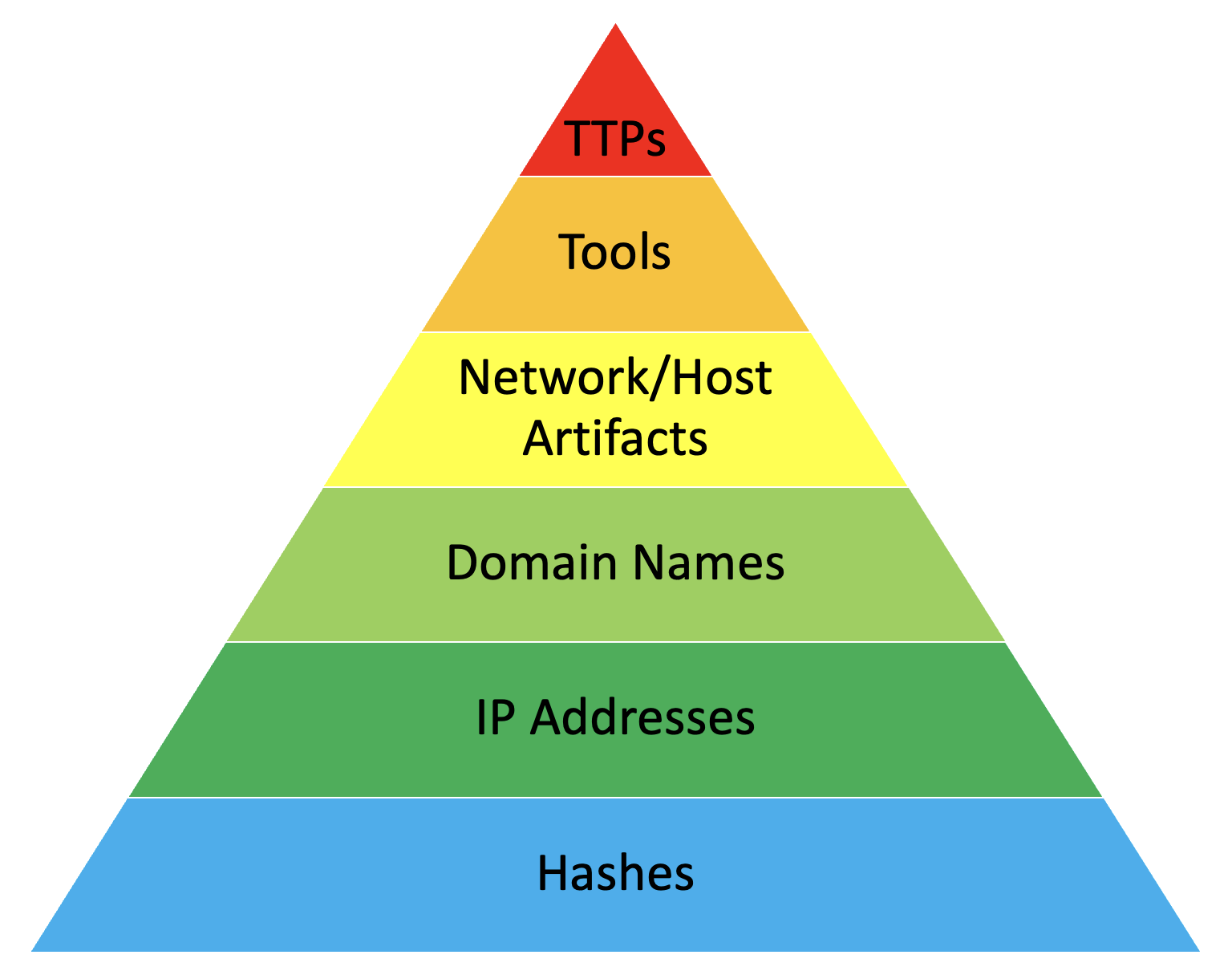
The Pyramid of Pain
Resources
The following resources expand on topics covered in this chapter.
Tactics, Techniques, and Procedures
NIST Special Publication that provides a definition of tactics, techniques and procedures
Chris Johnson, Lee Badger, David Waltermire, Julie Snyder and Clem Skorupka, "Guide to Cyber Threat Information Sharing" NIST, October, 2016
Read MoreMITRE ATT&CK
An overview of the design for MITRE ATT&CK, including object model definitions and design choices
Blake E. Strom, Andy Applebaum, Doug P. Miller, Kathryn C. Nickels, Adam G. Pennington, Cody B. Thomas, "MITRE ATT&CK: Design and Philosophy" MITRE Corporation, March, 2020
Read MoreIntroduction of the Impact tactic in MITRE ATT&CK
"Updates - April 2019” MITRE Corporation, accessed February 29, 2024
Read MoreA complete list of the data sources present in MITRE ATT&CK
"Data Sources” MITRE Corporation, accessed January 12, 2025
Read MoreA breakdown of Russian cyber-offensive activity and its origins across federal security and foreign intelligence services (FSB and SVR) and other government and military organizations
"Russian State-Sponsored and Criminal Cyber Threats to Critical Infrastructure" CISA, May 9, 2022
Read MoreATT&CK Tools
A list maintained by MITRE of projects that allow you to access, extend, transform and operationalize the ATT&CK framework
"ATT&CK Data & Tools” MITRE Corporation, accessed January 12, 2025
Read MoreThe DeTT&CT project, for analyzing the quality and coverage of data sources in relation to MITRE ATT&CK
"DeTTECT” GitHub, accessed January 12, 2025
Read MoreThe ATT&CK Navigator, for overlaying data on the MITRE ATT&CK matrices
"attack-navigator” GitHub, accessed January 12, 2025
Read MoreThe D3FEND project, a companion to ATT&CK that lists defensive techniques and countermeasures
"D3FEND" The MITRE Corporation, accessed January 12, 2025
Read MoreThe Cyber Kill Chain
An introduction to Lockheed Martin's Cyber Kill Chain, including details of each of its stages from an adversary and defender perspective
"Gaining the Advantage: Applying Cyber Kill Chain Methodology to Network Defense” Lockheed Martin, 2015
Read MoreThe Diamond Model of Intrusion Analysis
The original research paper detailing the structure, philosophy, and applications of the Diamond Model
Sergio Caltagirone, Andrew Pendergast and Christopher Betz, "The Diamond Model of Intrusion Analysis” US Department of Defense, May 7, 2013
Read MoreThe Pyramid of Pain
David J Bianco's blog outlining the usage and application of the Pyramid of Pain
David J Bianco, "The Pyramid of Pain,” last modified January 17, 2014
Read MoreDetails of the Microsoft Windows security feature, Credential Guard
"Credential Guard overview” Microsoft, September 5, 2023
Read MoreA joint advisory from the United Kingdom's National Cyber Security Centre (NCSC) and the United States' National Security Agency (NSA) detailing the threat group Turla's abuse of OilRig infrastructure
"Advisory: Turla group exploits Iranian APT to expand coverage of victims” NCSC and NSA, October 21, 2019
Read MoreAn example of a static user agent implemented in NCC Group's ScoutSuite tool
accessed February 29, 2024
Read MoreAnother example of a static user agent implemented in SpecterOps's AzureHound tool
accessed February 29, 2024
Read MoreCode in SpecterOps's SharpHound tool designed to create consistently named output files
accessed February 29, 2024
Read More